| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
October 2018
How IRSF Predators are Evolving their Fraud Attacks on the Weak and Unprotected of the Telecom Serengeti

The fortunes and failures of telecoms follow the laws of the animal kingdom.
Take, for example, the life of a wildebeest in the Serengeti Plains of East Africa. Each year about 1.7 million wildebeest migrate in search of rain and the best grazing lands in a circular journey from south Tanzania to Kenya and back again.
Wikipedia estimates about 250,000 wildebeest die on the trip north to Kenya. Death is usually from four causes: thirst, hunger, exhaustion, or attacks by predators.
Now, seeing wildlife films of lions hunting wildebeest, we’re led to believe that the wildebeests are easy targets for the lions.
However, facts suggest otherwise. Wildebeests are amazing athletes who can run for long periods at 50 miles/hour. Meanwhile, lions can only run at a sustained speed of 30- to 36-miles per hour.
Another factor to consider: the Serengeti predator population is relatively small: some 3,000 lions, 1,000 leopards, and 8,000 hyenas. That’s a wildebeest-to-predator ratio of a high 142-to-1 — and it doesn’t even count the zebras, gazelles and other grazing animals the predators target.
OK, switching now to the tactics of telecom fraud predators, we begin to see the parallels. Most telecoms — like wildebeests — are equipped with good “speed”, in the form of advanced fraud control software, trained analysts, and techniques for detecting and blocking International Revenue Share Fraud (IRSF).
But, from a predator’s standpoint, attacking fraud-protected operators is a waste of resources. In fact, the telecom “wildebeest” population is so large the fraudster can patiently scan the herds to find the most vulnerable operators to attack. And just like a team of lions, the fraudsters use stealth and cooperate with each other to increase their hunting efficiency.
One man who’s made a career out of studying and stopping telecom fraud predators is Colin Yates, and we’re pleased to interview him again on Black Swan.
Formerly head of Fraud Management and Investigations at the Vodafone Group, Colin continues his life mission now as an independent consultant who trains fraud analyst teams and develops/sells fraud-early-warning databases.
In our discussion, Colin shares some startling research data and facts on how fraudsters are using automation and other techniques to fight back against the recent success operators have had in blocking fraud, particularly to high-revenue destinations.
Colin makes a passionate case for operators to improve and sustain their fraud control systems, defensive tactics, and fraud analyst manpower. So wildebeests who fail to keep up with the herd — BEWARE!
| Dan Baker, Editor, Black Swan: Colin, in a previous Black Swan discussion, you explained the role of PRISM, the IPRN database that you and FRS Labs have distributed since 2014. Can you give us a quick overview of its purpose? |
Colin Yates: PRISM is an IPRN Test Number Database, a called-number hotlist that tells an analyst with 100% certainty that the number called was advertised on an IPRN website. Before a fraudster runs an IRSF campaign, they will run test calls against these advertised numbers, so detecting those test calls serves as an excellent early warning of attack.
The operator, in turn, uses PRISM to hot list, or in some cases permanently or temporarily block calls on that number, and then investigate the device used to originate the call.
Some FMS vendors have now integrated PRISM in their systems with various notification methods, such as 24x7 alerts to analysts’ mobile phones. In some cases vendors have built-in clever visual representations to detail call count and duration when PRISM calls are detected.
| So how’s the use of IPRN Databases going? Is it helping to curb the IRSF problem? |
To be honest, Dan, when I first envisioned PRISM, I figured in two or three years’ time such IPRN Databases would disrupt the fraudsters enough to ruin their business case.
Well, turns out I couldn’t have been more wrong, in part, because the fraudsters have vastly increased the volume of IPRN numbers being advertised.
When we started back in 2014, the first database of IPR Test numbers we released contained 17,000 numbers. But now (September 2018) the total database contains around 1.4 million numbers, and we regularly purge numbers that have not been advertised over the past 2 years.
In July 2016, we added 14,069 new numbers to our database, but exactly two years later the list climbed to 90,350 new numbers, and these are IPRNs that have not been advertised previously!
Now we think it’s also important to track the sheer volume of IPRNs being advertised on the web. That number has gone up too. Recently we are consistently seeing over 300,000 IPR Test numbers advertised during each 2-week period. And this is accompanied by a significant increase in the IPRN Aggregators who are making these numbers available.
The graph below shows the steady growth in IPRN’s being advertised over the past year.
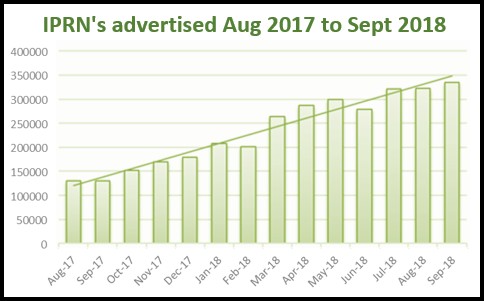
| Wow, the chart shows a pretty steep climb in only one year. |
Dan, the terminating destinations of the IPRN’s being advertised are also changing. There’s a move away from traditional ‘high risk’ destinations: the IPRNs in most of the top 15 high risk destinations are now being advertised less often.
If you compare PRISM data over time, you see that in January 2017, 42% of the database content were related to the top 10 fraud destinations (Cuba, Lithuania, Latvia, Somalia, etc.). However in September 2018, this percentage dropped to only 22% of the total database.
This is no accident. In my view, it’s a deliberate attempt by the IPRN Providers to avoid the number range blocking they experience going to traditional high-risk destinations.
In general, we’re now seeing an increase in many of the European destination numbers, such as Portugal, France, Spain, Belgium and Netherlands. Plus new destinations, such as the Philippines, Jordan and Tanzania, have moved into the top 20 high-risk destinations list.
So IRSF Fraudsters are making a trade-off. They are willing to shift traffic away from traditional high tariff rate destinations to lower rate destinations that are less likely to be detected and blocked.
Another issue entirely is that the numbers we see are probably only 60% to 70% of the total numbers they are advertising overall. The rest are advertised on so-called “dark websites” that evade the search engines.
Plus, the numbers that appear often come from new number ranges just introduced. So the fraud control community doesn’t even know such ranges exist nor who the legal owner of the numbers is.
| Where do these new number ranges come from? |
The numbers come from many sources. And remember, aside from phone calls, operators also allocate numbers for legitimate VAS (Value Added Services), things like Content Services, Fortune Telling, Adult Content, etc. The caller pays to access these services through their phone bill, and their telephone company reimburses the content services provider for providing this content.

However IPRN Providers continue to try and disrupt the blocking of known IPRN’s by including valid non-VAS numbers in their advertised test numbers and rate cards. For example, the numbers they select are often busy terminating numbers, such as hotels and Government Offices where blocking them would result in customer complaints, and pressure from within the CSP to remove number blocking.
We also noticed an increasing number of Mobile Station Roaming Numbers (MSRN’s) being advertised by the IPRN Aggregators. More than 5,000 of the currently advertised numbers (2018) in the 2018 PRISM Database are MSRNs, with over 17,000 MSRN’s in the total database.
An MSRN fraud (IRSF) utilises the E.164 defined telephone number that is used to route telephone calls in a mobile network from a GMSC (Gateway Mobile Switching Centre) to the target Message Switching Centre (MSC). The MSRN is allocated to a subscriber during Message Transfer (MT) call handling and is released when the call to that subscriber is established. Every Mobile Network Operator has MSRN’s allocated to it and these numbers cannot be used to terminate local calls.
However, IPRN providers still advertise these MSRN number blocks on the internet for IRSF purposes. While it’s possible that specific MSRN numbers could be filtered out of the signalling between the A and B party MSCs, there’s also a significant risk that blocking these MSRNs might prevent a roaming customer from receiving calls.
| It must be a challenge keeping up with all these number categories that the IPRN Aggregators post on-line. |
It is, especially when 90,000 plus new numbers are being added to IPRN websites each month. Many of these are replacement numbers for those already discovered by CSPs and blocked. Some IPRN Aggregators are changing out between 50 and 60% of their published numbers each month.
Some carriers rely on blocking (or hot listing) numbers that have previously been used during IRSF attacks. However, that’s not enough because once IPRN Aggregators discover their numbers has been blocked, they will generally not use it again because they have an endless supply of other ‘clean’ numbers to choose from.
| In the past, we’ve discussed IRSF attacks where the routing of the call is “hijacked” away from the called destination. What’s the latest on that kind of fraud? |
Yes, Number Misappropriation or Number Hijacking continues to be a problem and, in my view, will remain an issue for some time to come.
Number Hijacking often occurs when IPRN Aggregators advertise country numbers where they have no relationship with the number range owner.
Remember, the only way an IPRN provider can make money here is when termination occurs in a country or network where the IPRN provider has a relationship with the terminating operator. But where hijacking is involved, they have no such relationship with the legitimate range owner, hence the need to redirect the call.
Hijacking, then, is enabled by a middle provider somewhere in the network routing chain who redirects the traffic from the called number away from the destination country, to a location where fraudsters have their criminal partners who can terminate the call.
| So how can legal range owners protect their numbers from being the unwitting target of IRSF calls? |
I know this activity seems outrageous and unlawful, but actually the International Telecommunications Union (ITU), who take the misuse of telephone numbering resources very seriously, has no authority to prosecute those misusing the resource.
The only remedy we currently have is to pressure IPRN Aggregators to remove numbers from their websites when they have no authority from the number range owner to use them.

Now I’m pleased to report that the Pacific Islands, who I’ve worked with for several years on solving this problem, have succeeding in moving themselves off the top 100 fraud destinations list.
To get to this point requires a persistent effort because some IPRN Aggregators flatly refuse to let go of those numbers. Another approach is to contact ISPs who host the websites where these numbers are advertised unlawfully, and ask them to take the IPRN websites down due to illegal content.
However, the number providers feel safe knowing there’s not a lot that can be done to enforce number removal. The number providers also hide behind the fact that they sell legitimate paid information services to the public.
We have been successful within the industry however to find support from a number of Law Enforcement Agencies, including Europol, who are now involved in investigations to identify not only those who make the IRSF calls, but also those who are providing the numbers used to commit IRSF.
| Is there anything operators can do to block the hijacking where it occurs in the traffic chain? |
Well clearly when a destination’s price is much lower than its cost of termination, that should cause some alarms to ring.
Unfortunately, automated routing is actually helping the fraud to spread. Least cost routing systems are often set to select the cheapest route from ‘A’ to ‘B’ on a daily basis, so the fraudsters take advantage of this to steer traffic.
A common ploy of unscrupulous transit carriers is to forward traffic via untrusted routes that are known hijacking points. We do have information that some Telecom employees around the world are also rewarded for filtering out calls to certain destinations and sending these in a different direction for termination onto an IVR.
| In my recent telecom wholesale research study, we noted the growing versatility of global private networks. For example, DE-CIX, the largest internet exchange in the world, now offers cost effective private networks that a community of trusted users can set up for themselves and set their own security parameters for. |
Agreed. There’s lots to be said for trusted networks. As soon as you insert a bad apple in the mix, the call may never get to the destination it was intended to go to, and you’ve got IRSF fraud. If you can pass your calls off to trusted partners, that removes a lot of the risk.
| Of course, the other key weapon in the fraud control fight is getting operators to cooperate in solving the industry problem. |
Yes, and on that front the i3 Forum is doing some very good work amongst the Wholesale Carriers to implement some anti-fraud controls within its membership.

Happily there’s more focus now on treating fraud as an industry problem. Common platforms help. The i3 Forum has just launched a Code of Conduct to combat fraud in international telecoms, and this CoC sets out the principles the carriers have committed to reduce fraud.
This CoC requires each i3 Forum carrier member to comply with certain deliverables around reporting and investigating fraud, along with stopping payment to the fraudsters wherever possible.
But not all industry cooperation succeeds. At a GSMA conference a few years ago, we made a strong case for stopping all IRSF payments on the basis that these payments were the proceeds of crime, and what we were actually doing was supporting these fraudsters to commit a crime and engage in money laundering.
A good half of the industry agreed with us. Trouble was, some Operator members said “no” and some obtained different legal opinions to those we had obtained. So there was a conflict, and we could never get past this disagreement.
| What’s your assessment of fraud management systems these days, Colin? |
There’s no doubt Fraud Management Systems (FMS) have improved considerably over the past 5-10 years and the detection rates generally are at levels we would not believe possible as young fraud analysts many years ago.
The cost to implement an FMS has also come way down. If you go back 10 years, it was almost impossible to buy a fraud solution for less than one million dollars. Now the costs have dropped considerably and it’s encouraging operators to make that investment.
However, in my view, carriers should be very careful how they apply automation to number blocking.
The danger is that many CSP’s are now relying on automation to justify a reduction in Fraud Analysts. But a team of experienced and effective Fraud Analysts should be a requirement in every telecom business.

Fraud analysts are great resource when you consider a fraudster can steal in one weekend what a fraud analyst makes in a year.
Compounding the problem: very few fraud analysts are coming into the industry now, so the supply of knowledgeable and experienced people in these roles is diminishing.
Automation only takes you so far: you can’t rely on it to stop 100% of fraud problems. You still need a good fraud analyst to analyze the information coming out of that automation — and also recommend where the business needs to improve controls to stop the fraud that’s happening, and protect against future attacks.
Insider fraud is another area where fraud analysts can be vital guardians. Insider fraud is not easily detected because it requires a deep knowledge of an operator’s systems, so internal experts can investigate this insider fraud in ways that artificial intelligence and automation cannot.
I know that carriers who use soft PBXs feel somewhat more protected from hackers because their longer passwords are harder to discover by brute force methods. But once a fraudster targets you, all it takes is one dishonest insider to provide the necessary information and support to facilitate a fraud.
So carriers who don’t properly staff their fraud teams are asking for trouble.
| Sounds like the IRSF fraudsters have stepped up their game on the automation side. |
It’s very true, in fact, the fraudsters are probably better at automation than operators.
They will make two or three calls to test. If you block the test number, then they will move on to another country till they find a test number that’s not blocked.
An IRSF attack will generally last 2 or 3 days. The majority of attacks start around 8:00 PM on a Friday night and stop Monday morning. It’s obviously calculated to count on the reduction of resources on fraud teams over this period.
Some of these attacks are 6 months in the planning, particularly when they need to set up the IRSF through internal fraud. Many IRSF calls are computer generated and timed to move in call duration and call destination to try and avoid detection. Obviously the intent of the Fraudster is to maintain their ability to make these calls for as long as possible, and generate as much illegal revenue as possible. We just have to keep finding ways to disrupt this activity.
| Colin, as usual, your research and ability to dissect key fraud control issues is extraordinary. I’m sure this story will become invaluable reading for fraud analysts around the globe. |

Copyright 2018 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum

