| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |

Advanced identity verification and KYC programs have been active in the banking industry for years. But where can telecoms go to get help building such solutions tailored to its unique needs?
Well, one firm that’s actively helping carriers get equipped with advanced subscription/application fraud systems is San Jose-based FICO, a $1 billion-a-year software, analytics and fraud-fighting firm that’s been around since 1956.
FICO is well known in the U.S. market: consumers talk about getting a high “FICO score” as a mark of having good credit. But FICO’s public persona as a risk scoring expert is a bit misleading, because FICO also develops and sells behavioral and analytics software to enable enterprises to do their own risk scoring and decision-making.
FICO’s Falcon Platform was originally developed for the credit card transaction market, and it’s a pioneer in the use of AI and machine learning technologies. In the last several years, FICO has also developed a range of new technology in the application fraud prevention sphere.
I interviewed two FICO experts: Mel Prescott, Principal Consultant in FICO’s telecommunications practice and Andy Procter, a consultant on the FICO Advisors team.
We head a great, free-wheeling discussion on: subscription fraud best practices, advanced ID verification tools, and the challenges telecoms face as they ramp up to rival systems in the banking and card industry. Their 9 recommendations are a must-read for any telecoms looking to improve its subscription fraud and ID verification programs.
| Dan Baker, Editor, Black Swan Telecom Journal: Mel and Andy, welcome. You’re both working out of the U.K. but in different departments of FICO. Can you briefly explain your roles at the company? |
Mel Prescott: I’m the telecom industry consulting lead for FICO with 20 years of analytical roles at telecoms behind me. I’ve held credit risk and fraud management positions at Orange, EE, and also Bank of America, so I’ve delivered decisioning platforms, fraud tools, analytic models and led enterprise-wide fraud initiatives.
I’m here to provide subject matter expertise and represent the view of the customer to ensure FICO is delivering the solutions telcos need. Every B2C company is focused on how to improve its relationship with its customers, and FICOs aim is to be the go-to decisioning platform for B2C companies looking to optimise their consumer interactions.
Andy Procter: Dan, my background is in financial services and retail, and over the years I’ve been involved in a number of telco engagements. And when we do consulting work, we also bring in telecom-dedicated folks such as those on Mel’s team.
We’re not just doing banking in a different environment: we are using telco knowledge as well.
I’m actually on the FICO Advisors team with around 45 people. In that team there’s a life-cycle team that looks after originations, account management and collections. Then there’s the 15-person group of fraud advisors, and I’m a part of that group.
All of us are ex-fraud or risk managers so we have the user industry experience and we advise clients on a wide range of fraud issues regardless of whether they use FICO software or not.
| Great, so to begin, I’m curious what your assessment of telecoms is? How advanced are they in subscription fraud and identity verification? |
Andy Procter: I’d say the telco space is a mixed bag. Certainly in many key areas they are behind the financial services industry, which has historically been FICO’s home ground.
But while bringing financial services expertise in is relevant, there are several other issues telcos need to address to achieve excellence in ID verification and subscription fraud management. They need to:
- Organize and realign their fraud and credit teams for maximum effect.
- Invest in a few crucial identity tools and analytic software.
- Build an internal capability to analyze subscription/identity fraud methods and improve front-line decision-making and onboarding procedures.
- Adopt subscription fraud best practices and create benchmarks to measure progress.
To expand on these points, Mel and I came up with 9 recommendations we think will enable telecoms to build out a strong capability. So let’s go through them one by one:
1. Improve ID verification via Selfie with “Liveness” Detection
Mel Prescott: Dan, one of the key things you want to do at point-of-sale is to verify: is the person filling out the application the person they say they are?
And as the sale of mobile devices on-line steadily grows more important, you’ll need to verify IDs both on-line as well as at the retail store.
It’s in this area of digital ID verification where FICO recently acquired a solution we call FICO Falcon Identity Proofing.
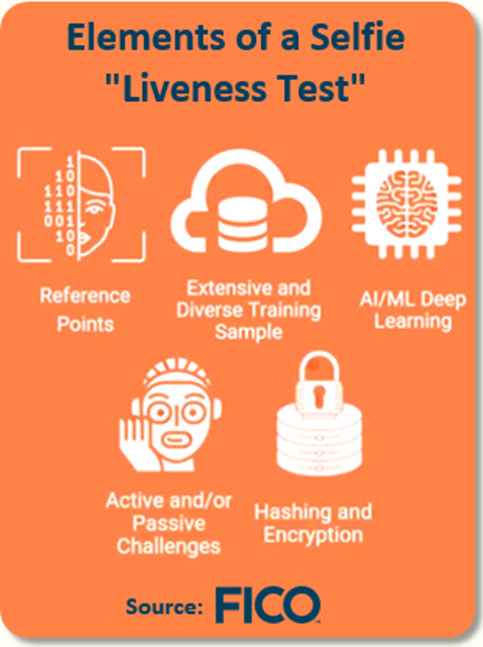
FICO Falcon Identity Proofing allows, through the digital journey, to take a selfie and compare that accurately with a scan or picture of a government-issued ID document.
This new technology not only uses the latest face-detecting algorithms to analyze the selfie, it also includes a “liveness test” to make sure the selfie isn’t just a picture of a picture. Other features such as document capture, hologram detection, and real time corroboration ensure organisations take a balanced approach to security and user experience.
The technology verifies identities in real time, by establishing Proof of Identity, Proof of Possession and ID corroboration.
2. Use Digital Identity Authentication to Reduce Friction
One of the issues with self-care portals and customer care phone interaction is you’d like to quickly get down to business with the customer: taking away the friction of remembering passwords or asking too many questions to verify the customer’s identity. You also want to reduce the risk of social engineering, I was surprised to learn in a recent discussion with an African CSP that it was common practice for agents to prompt customers with clues if they couldn’t remember their credentials.
It’s here where biometrics, such as voice recognition technology, has become extremely useful in the banking world. And if implemented right, voice recognition delivers greater ID verification since passwords can be compromised. One of the things you can do here is have the customer simply say “My voice is my password”, “FICO is awesome”, or something like that.
It’s as simple as that. You can also follow-up with various methods of multi-factor authentication. Perhaps you can send a token to a mobile device and use digital finger-printing with the device, or look at keystroke analysis alongside other behavior.
This combination of biometrics, multifactor and behavioral authentication enables a comprehensive, adaptable, and proportionate approach to be taken with regard to security and the customer experience.
3. Use Machine-Reading to Verify Applications at PoS
A key subscription fraud concern today is that essential fraud checks cannot be done on the spot. They are often accomplished after the sale is posted or “post-activation”. The device is typically activated or shipped to a customer right away, then a day later the full fraud check is performed.
But given the high losses in mobile phone thefts that firms like Verizon are experiencing, there’s a great need to deliver fraud decisions in real-time.
For this purpose, FICO has developed a machine-reading technology to rapidly capture and process the info on the application form. This OCR-based analysis tool can be used for both on-line applications and hand-written applications at a retail store.

The key advantage is that typos are spotted right away; digits are also checked to detect wrong postal codes and phone numbers. This results in data matching algorithms being more likely to match the right individual at, for example, a credit bureau.
Then, once the application is filled out, an image is captured of the person’s face and that’s merged with the application document as an attached file.
Not only does this enable real-time analysis, the machine reader does away with the persistent problem of receiving applications where an important field is missing, or in some cases, the entire document ends up being a blank sheet of paper.
Utilisation of this technology helps to reduce identity fraud losses, it can also be used to clean application data and speed up that process by populating name, address and other fields by reading the data from the ID document. It also reduces the opportunity for dealer collusion by taking that digital identity decision away from those in the store.
4. Do Real-Time Identity Analytics on the Credit Application
The real payoff to getting a clean application form is it sets up a real-time analysis of the data.
For this job, we use a tool called FICO Identity Resolution Engine. It takes the many different fields in the application form — delivery address, email address, their devices being used, phone numbers, and various entities / attributes presented during the application process — and compares them to recent applications. It can even look across your entire customer base to find any links to these bits of data.
The idea is to discover non-obvious relationships between the application being reviewed and all previous applications of existing customers.
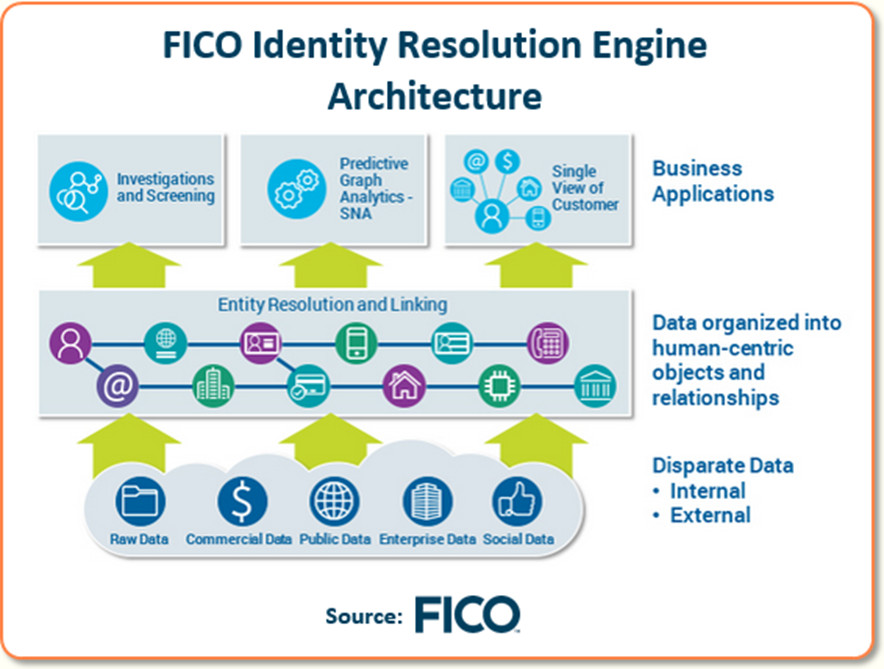
For instance, you might find the postal code for this delivery address is fraudulent. Or maybe there’s a link to a phone number of an existing account, but that existing account signed up only two months ago and is already in collections. In short, it looks like a first party fraud with no intention to pay.
It’s really about being smart in finding links between the various data fields in the application, then extracting the metadata from all those different names to provide a risk score for that application.
Andy Procter: Dan, this Identity Resolution Engine goes way beyond looking for a direct match. There’s a social network analysis in there that allows the analysis to look for matches that are one, two or more degrees of separation away.
We can go up to 10 degrees of separation but any separation beyond 3 or 4 degrees often yields lower incremental benefit.
As an example, maybe my email address does not connect directly to Mel’s. However, there’s someone one or two degrees away who links to both Mel and me.

OK then, how can we use this info? Well, when you bounce the application data against this social network analysis, maybe you find the person is linked to a number of bad debt accounts — accounts that have gone bad, and gone bad fairly quickly.
As you can imagine, having such depth of analysis — as the application is being reviewed — is invaluable. You can even model the tool as you’d like — say, assign weights based on how direct the relationships are between two email addresses.
Another beauty of the tool is its use in fraud investigations. The data can be looked at graphically — quite useful when working with police and investigators who are trying to decipher fraud rings.
5. Better Align the Fraud and Credit Risk Teams
Andy Procter: OK, Dan, now that Mel has walked you through the key software tools we recommend, I’m now going to make some recommendation on best practices and organizational issues.
To begin, at FICO we strongly believe subscription fraud should have a single owner, but at telecoms that’s often not the case. You have folks in a group risk/security function who might look after traditional ID theft and security, and the fraud control function resides in that team.
However there’s usually another team looking at the credit risk problem, and they oversee the first part of the fraud problem — screening out the people who have no intention to pay.

Unfortunately, these two different teams don’t always work together as smoothly as they should. The credit guys are typically brilliant at data analysis, but they don’t know fraud — they don’t always have a fraud mindset.
Meanwhile, the fraud guys really understand the fraud issues, but can’t manipulate data so well.
So there’s a great need to get these two areas better aligned with each other.
We typically see somewhere between 15-30% of a telco collections book actually being due to no intention to pay. It can be a grey area whether to class this as fraud or not, but the fact is it will be uncollectable debt, the device has been lost and it will impact the bottom line.
6. Build Up your Post-Book Fraud Analysis of Subscribers
In the years past, a telco would check for post-book subscription fraud by seeing if the customer was making his monthly postpaid payments.
But more and more, the organized fraudsters are making the first payment for the device. And the key reason is: they are not looking to just steal a mobile device, but to commit a bigger financial crime.
Now to conceal their fraud a bit longer, they might pay the first monthly payment, maybe the second. To better analyze the problem, we recommend looking at the usage pattern of the new subscriber. Are their calling patterns normal? What would a genuine person do?
If all their usage is high revenue, international, or premium rate numbers, that’s a very strong indicator. So as you combine all these factors together, you start building your primary detection focus at the point of sale — and prior to account activation.
But, just as important, you need to follow a subscription fraud monitoring plan for post-book too. So if you missed the fraudster at first, you can detect him soon thereafter.
7. Constantly Feed Case Intelligence Back to the Fraud Team
In the rush to solve fraud cases and move on to others, we tend to forget how important it is to provide feedback on problems discovered.

Simple example: an account goes into arears early, so collections tries to make contact with the customer. But they can’t connect because the email address doesn’t exist.
Now when something like that is discovered, there needs to a systematic way — or at least an operational process — to get that knowledge back to the fraud team.
But if you close the case without feeding back the intelligence, you’ve failed to prevent a future sale where the email address on an application was invalid and was not tested.
It’s all about having that intelligence at an earlier point where you can make better use of it.
It also speaks to the fact that the fraud team should not be acting in isolation, but should be collaborating with other areas such as collections teams. The collectors can stick to handling collections activities to those accounts they may be able to collect on, and leave those that are fraudulent to the fraud team. The collections team will appreciate their improved success rate.
8. Build Intelligence into Your Subscription Fraud Models
In recent years, fraud prevention and ID verification have greatly improved thanks to the new biometric, analytics, and identity detection solutions.
I’ve discussed some of FICO’s breakthroughs. And other firms are also breaking ground. NuData Security tracks a user’s on-line or mobile typing or data entry behaviors to verify the customer is who they say are. LexisNexis has a large network of business partners to keep daily track of anonymous identities as they visit websites.
Now all this information is being used to deliver a score to the telco, and that score is used to inform fraud and credit decisions.

This is all good stuff. And identity detecting firms have also done a good job in geo-location and data enrichment. Have we seen this email address before? Was it associated with this person?
Telcos can take the score and the additional contextual information for use in rules and models and can utilize their data scientists to build models. They can also bring in FICO, as we have many years of experience of building machine learning models.
Another advantage of growing your own intelligence is it enables you to ask the customer a very minimal amount of information so you reduce customer friction.
9. Get Advice from Experts in Banking & ID Fraud Detection
Dan, companies who maintain biometric solutions are usually not staffed with ex-fraud managers to advise their clients on how to operationalize subscription fraud.
But FICO is different. We are one of the few solution firms who actually help companies build their own internal ID verification and fraud detection capabilities.
Our consulting expertise is often most appreciated when it comes to answering client questions on best practices issues and getting answers to questions like:
- Who is actually going to work the cases? Sure, the solution’s case manager creates alerts, but once the alert is on the screen, what are we going to do with it? What actions can they take?;
- How are we going to know if we are performing well?; and,
- When we make rules, how do we know what a good rule or a bad rule look like?
Another issue: sometimes clients with a solid case management tool in place lack a good process for getting consistent answers for risk decisions, in part because it depends on how much risk a customer has an appetite for.
| Mel and Andy, thanks for these splendid recommendations. To finish out our discussion, I wanted to ask you about how you deliver your software and consulting to the customer. Can a telco buy one solution at a time? |
Mel Prescott: We can do things on a standalone basis, and the advantage of our system is that our solutions are built on a common platform. This enables telcos to build in LEGO building-block fashion, one use case at a time, and everything they build across the organization has a common underlying platform that enables them to share data, analytics and customer strategies across functions.

And there’s no conflict with having one FICO platform serving different business units across a customer’s organization. For instance, both credit and fraud teams may benefit from having a common platform that enables different applications to be deployed. This can help break down barriers between teams and ensure the impact of decisions across multiple business areas is understood and managed.
Here in the UK it’s quite common for telcos to provide an unsecured personal loan as an instrument to finance device purchases. This falls under FCA regulation and, as such, requires specific checks, such as KYC to be satisfied. All these different use cases sit in the platform and can be plugged in.
Solutions are increasingly supplied via a fully managed cloud service, providing the highest levels of security, scalability, compliance, availability and flexibility. By managing infrastructure, applications, operations, and solutions, FICO cloud managed services empower you to focus on what matters most: innovation and business results. Equally, we can offer on-premise deployments if our customers prefer to manage the software themselves.
For my perspective on FICO’s ideas on subscription fraud for the telecom industry, I’d like to point you readers to a 5-page paper they can download entitled, What is Telecom Subscription Fraud — and How Can You Fight It?
Andy Procter: On the solution side, Dan, when FICO is bringing in software, our advisory team guys are the ones who help implement the solution — we help the client get the best use of the solution by having them consider all the aspects of how the solution will fit into their strategic and operational goals and constraints.
If there are FICO technical solutions being implemented, we come in at the very start of the project and work in parallel with the product implementation team.
As for consulting, we might go in to do an overall fraud assessment. Or it might be they have a particular problem. Maybe they are launching a new channel or are looking to expand their existing digital channel, or are experiencing an increase in fraud occurrences — we can go in and figure out what’s needed there.
| Thank you, Mel and Andy. Your advice is very timely given the rising importance of identity verification and subscription fraud in telecom today. Good luck as you engage with clients. And look forward to hearing of your further observations in future Black Swan discussions. |
Copyright 2020 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum



