| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
March 2021
Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking

How serious a threat does IoT security pose as a gateway to fraud and other damage?
Well, consider this: International Revenue Share Fraud (IRSF) costs telecoms alone close to $5 billion a year in fraud losses. And yet history tells us that to stop 80% of IRSF attacks entails monitoring the output of one kind of device: hijacked PBXs.
However, with IoT, not only will there be 100 billion IoT devices deployed, the variety of those IoT devices explodes to security panels, traffic signals, connected cars: any smart device becomes a potential gateway to fraud or other damage to enterprises of all types.
Fortunately, help is on the way. The first priority is to simply understand the IoT security threats that are coming at us from all different directions.
Subex is a company committed to gathering this vital IoT threat intelligence. Several months back we interviewed Kiran Zachariah, VP of IoT Business Solutions about Subex’s IoT honeypot network, the largest in the world.
Now, you can’t just drop a honeypot anywhere on the internet and expect good results. Subex is strategic about where to best attract bad-actor “bees”. Today, its network collects traffic in 62 cities with sites chosen for having one or more of the following attributes:
- A landing center for submarine cables
- An internet traffic hotspot
- Home to multiple IoT projects & endpoints
- Diverse technology environments
- Home to connected critical infrastructure projects
- Academic or research centers focusing on IoT
- Places that multiple future IoT projects will be hosted.
Daily, Subex registers and analyzes over 3.5 million attacks from this honeypot containing over 4,000 physical and virtual devices covering over 500 device architectures and varied connectivity flavors.
As you can imagine — given the mountains of data collected and the growing scale of IoT projects — security practitioners, decision makers, and governments are having a tough time keeping up with the latest IoT security trends.

So now Subex is publishing quarterly Threat Landscape reports to update everyone. To download the latest such report, click the image at right.
In this conversation, Kiran not only gives us some of the latest IoT security trends, but also provides an inside-look at how Subex’s research and monitoring teams coordinate to deliver a full-service IoT and OT security program.
| Dan Baker, Editor, Black Swan Telecom Journal: Kiran, what’s your current assessment of IoT Security? |
Kiran Zachariah: Dan, in the last several months of 2020 we saw plenty of enterprises and telcos get breached. It was a tough year, but much learning took place, and that experience will make IoT more secure.
One important new trend is a strong convergence of security environments that merge IoT --security and OT (Operational Technology).
We recognize today that there is no way you can understand IoT security on a standalone basis. We began with IoT and then evolved toward OT. OT is crucial in industries such as manufacturing, oil and gas, higher education, smart cities, and utilities.
We see a lot security problems occurring on the OT side, especially in converged environments that impact the IoT environment. That’s why we need to look at all sides.
| Can you give us an example of an industrial cybersecurity threat or case? |
Well, we are now protecting the cybersecurity of ships at sea. Subex has teamed up with SkyLab, a leader in industrial IoT and 5G Multi-Access Edge Computing (MEC), to protect ships and maritime infrastructure.
In fact, our honeypot research discovered that ships were attacked almost 1.5 million times in the last 30 days. Of these, over 64,000 attacks were highly sophisticated and carried out using complex malware and breach tactics. Very recently a cruise ship was cyber-attacked. Also, off-shore oil rigs are being threatened.
Targets for these attacks include datacenters, command and control infrastructure, navigation systems, power, and life support systems among others. There are also secondary threats such as: loss of shipping days, delays in transit of goods, damage to critical infrastructure, loss of either customer or commercially sensitive data, and ransom demands.
By the way, in the Middle East there are real pirates who attack ships. And there’s evidence that these groups are actively moving into cyber-attacks.
In one incident off the coast of the U.S., hackers tried to take over the navigation system of a ship and ram the vessel into a port. Fortunately the crew was able to regain control and avert any damage.

|
Being an ex-Navy sailor, this maritime cybersecurity interests me. When I served aboard a small oil tanker, we used to sail alongside huge aircraft carriers to refuel them with jet aviation fuel. The ships would sail only
60 meters apart, so to lose navigation control to a hacker at that time could
cause a catastrophe.
Now laymen like myself are in the dark about what security research teams actually do on a day-to-day basis. Can you explain how Subex organizes its internal effort? |
Sure, let me break it down by each team’s mission. It will certainly give your readers a better picture of all the factors go into researching malware in IoT and OT.
1. Malware Research
Malware Experts are our biggest group of researchers overall. These folks study the insides of the malware. They tear it down and find the key code lines in the malware that cause the damage. We not only need to know the specific types of malware, but also the way the malware’s code is evolving.
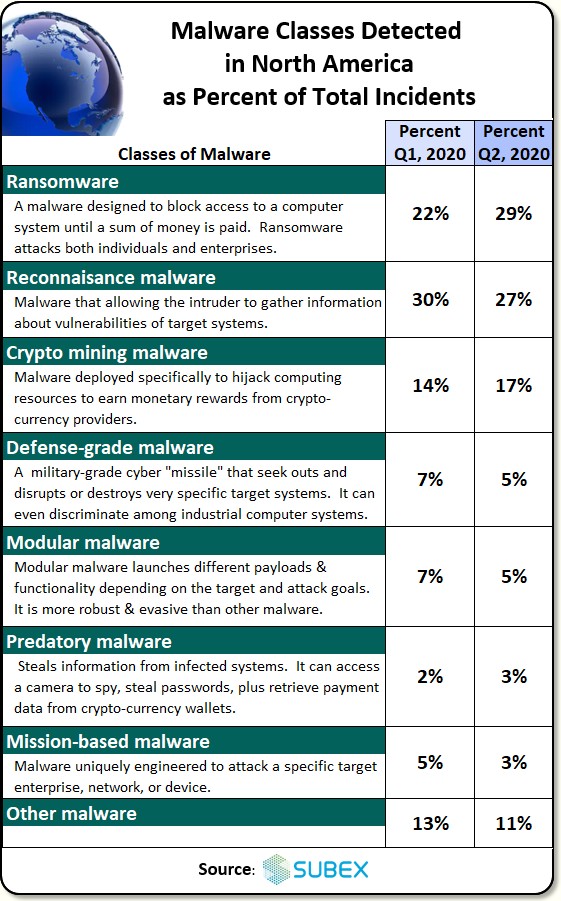
Actually, there are many varieties of malware out there. See the chart below showing the percent of incidents we detected for various malware attacking North America, the biggest target country we’re seeing these days:
Now in studying the malware, we not only figure out how it works, but also learn how the bad actors manage multi-stage attacks.
For instance, it’s quite common to see two waves of attacks conducted against IoT targets. The first wave might last for 95 days, then a second wave comes. To the casual observer, these attacks seem random, but they are coordinated — there’s a definite plan.
So by understanding how they launch these attacks, you’re able to predict where future attacks are coming from. There are tell-tale signs an attack is coming. Sometimes we will pick up some early variants of malware which we know are laden with bugs and so there’s a history behind the particular version of malware.
Then we notice actors buying this well-recognized malware and converting it into something that works better — and will eventually cause us more trouble.
2. Threat Research
Threat Researchers are another group on the Subex security team. Their job is to figure out how much damage a malware will do. How do we contain it? How can we detect it early on? And how can we disrupt its operation? By identifying the places this malware is coming in, we can figure out how to limit the geographies where it is used.
But discovering the origin is not so easy. For instance a North Korean hacker might purposely leave some notes in Russian: it’s a way to confuse researchers about the origins of their code.
The behavior of the malware is often a good indicator of its origin. Another clue is the programming language used. The coding syntax a developer consistently uses also gives us a good idea who is behind these attacks.
So we maintain a library of malware authors who originally authored the malware — as well as the actors who added a few lines of code. Even though a person or group developing a malware is anonymous, their history can be tracked and it becomes very useful intelligence for security.
Many of the actors also get involved in targeted attacks on critical infrastructure of governments or corporations.
3. Malware Distribution Research
Malware Distribution Research is crucial because the criminals are commercially sophisticated: they operate their own black markets for trading the malware and code among themselves. So our researchers focus on identifying the on-line forums and dark web sites where the actors are deploying or selling the malware.
Even though the original code was developed, say, in China, it’s just as critical to know who the global intermediaries are who are pushing this malware into the on-line forums where they are bought and exchanged, and then used for specific DDoS attacks or bulk attacks.
So when we capture info on the malware trading activity, it give us some early warning signs on how soon the next attack may occur or where we might expect to see new threats.
4. Metaforensics Research
Metaforensics Research is performing metatag analysis to see who may be developing or modifying the malware. The “fingerprints” are there to capture, but it requires diligent observation and research to extract meaning from that metadata.
The metadata analysis is also critical to figuring out how to respond to a particular kind of threat by a certain group of actors.
For instance, security people say, “Oh, I recognize that malware as APC38 and its origin is China, or maybe Vietnam”. Well, unfortunately such generic information is not specific enough to be very useful. You need to know who the behind-the-scenes actors really are — even specific to certain IoT environments.
What actors are the source codes coming from? Who are the players modifying the malware?
Frankly, this deeper metatag analysis gives us an advantage because not many vendors perform that level of analysis.
5. Client-Specific Research
Client-Specific Researchers are those people of ours who actively work for customers to detect specific malware or protect their particular infrastructure of security concern. Generally, the client gives us directions on what they would like us to do.
And this sometimes includes “ethical hacking” where we work on behalf of the client to identity their enterprise vulnerabilities from network, infrastructure, or device configuration views.
6. SOC-Based Monitoring
SOC-Based Monitoring includes teams who monitor the networks and infrastructure of our customers either remotely or on-site to detect and address threats and also analyze threat data.
7. Project Management & Honeypot Operations
In addition to all the other research activities, we also have the regular complement of PMOs, project managers and a team that runs the honeypot.
|
Thanks, this is a great breakdown, and certainly you only scratched the surface
of each team’s activity. The scope of the research is impressive.
Now I know your research is aimed at all enterprises, but it seems especially relevant for telecoms who are the unwitting intermediaries in these attacks. |
Yes, it’s very serious now. Our mobile phones and IoT devices are vulnerable to hacking at a personal level. At an institutional level, since telcos are the connectivity providers to businesses, their cybersecurity posture has wider ramifications for all industries.
Smaller telecom players are getting impacted more than the bigger ones. Fortunately, the telcos are proactive in containing these threats.
In the future, we’ll see lots of attacks coming from the satellite uplink and downlink. The trouble is the levels of encryption are relatively easy to break there. Other researchers have noticed it’s also easy to intercept traffic from satellites passing overhead.
The key threat is that telecom players become a key enabler of these big attacks: the data they hold and the devices that are being hacked.
This is why telcos have a big stake in IoT security. A lot of these hackers are people who have worked at telcos or at telco infrastructure firms so they already have substantial knowledge of what goes on behind the firewall.
At Subex we say telcos are at the front lines of cybersecurity. . . and also the first line of defense. On that front, we’re proud that we’ve recently become an exclusive IoT partner with Telefonica.
| National governments are another key sector. |
Awareness of the IoT threat to governments is just getting started in many countries, Dan. And it’s particularly important since certain countries are “launch pads” for cyber-attacks.
A high number of attacks, for example, are now emerging from countries that hire state-supported hackers to meet their geo-political objectives. So every country has a stake in preventing hackers from operating freely and in containing their activities.
To monitor suspicious activities and prevent hackers and malware from disrupting businesses, Subex has support personnel, such as those at our security operations center (SOC) in Bangalore.
We’ve had many discussions with the government of India — and given them recommendations in the past. The Indian government is working hard to support the IoT initiatives. And so the people are expecting improvements.
|
Thanks for this fine briefing, Kiran. The IoT security feels like a hurricane
that you know is coming. It’s caused major damage to small islands
on its path north, but it’s now headed toward a major city.
Nice to know firms like Subex are doing their analysis, forecasting, and protection: it will lessen the damage. |
Copyright 2021 Black Swan Telecom Journal
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


