| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
August 2019
Tethering Fraud: How Guavus Blocks the Pumping of Mobile Data Traffic and Tools Up to Deliver 5G Service Management

“Traffic pumping” is a great metaphor for telecom fraud.
When you hear the term “traffic pumping”, your brain can imagine an IRSF fraudster’s scheme to over-inflate the network by pumping thousands of voice calls through telecom pipes to a foreign operator at $10 a minute.
But “traffic pumping” is not restricted to voice fraud. It also applies to stealing mobile bandwidth, a practice called tethering fraud.
Now exactly what constitutes illegal tethering requires some clarifying. For instance, tethering isn’t stealing if a customer’s contract with its CSP allows it. Tethering fraud concerns unintended and uncontracted uses of tethering, such as:
- Unauthorized users/devices tethering;
- Illegal use of a wireless router SIM card in another device; and,
- Excessive users connected to fixed wireless broadband devices or such devices being outside the contracted rural area.
And given that 5G’s networks of small cells which will soon be pumping orders-of-magnitude more mobile data than ever before, shouldn’t we be paying some serious attention to the mobile data pumping threat?
We absolutely should. Trouble is, few solution vendors specialize in fighting tethering and mobile bandwidth-stealing. Fortunately, I recently interviewed two tethering fraud experts from the San Jose-based telecom analytics firm, Guavus: David Yates, its VP of Product Management, and Kent McIntosh, their Head of Marketing.
Our discussion is a great backgrounder on how analytics is being applied to next generation data threats. You’ll learn how tethering fraud occurs and how Guavus detects the problem. Also discussed are the company’s approaches to reducing data volumes at the network edge, IoT fraud concerns, and automating the healing of high-quality 5G data services.
|
Dan Baker, Editor, Black Swan: David, I know Guavus to be a telecom
analytics pioneer. I can say that with some authority because in 2014
I authored a 491-page TRI research report entitled Telecom Analytics and Big
Data Solutions.
And as I scan the names of the 41 companies profiled in that report, about half of them have exited the business, and Guavus remains one of a few pure-play-analytics firms still active in telecom. Then, just two years ago, you were acquired by Thales, the French aerospace giant in 2017. |
David Yates: Yes, Dan, telecom analytics has been our specialty from the beginning. The Thales Group (pronounced “talɛs”) is actually a multinational company (with 80,000 employees in 2019) serving aerospace, defense, transportation, and security markets. Headquartered in Paris, Thales did €15.8 billion of business in 2018.
Now, as you can imagine, Thales is involved in many digital transformation projects around the world so they are particularly keen in investing in advanced tech such as cybersecurity, IoT, network optimization, analytics, and predictive maintenance.
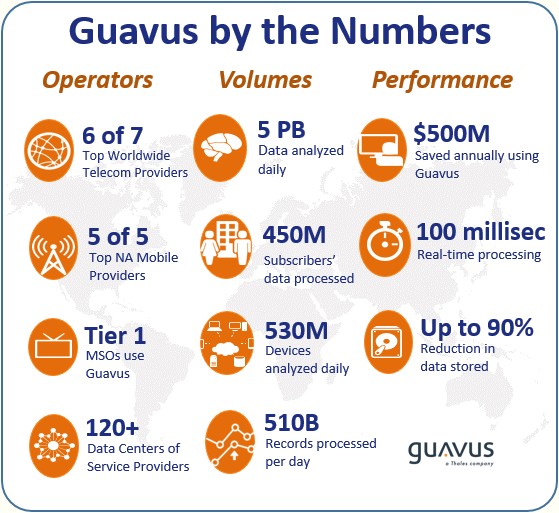
What attracted them to Guavus was our strong reputation in realtime Big Data processing. So today, at Guavus, we have 250 employees and the lion’s share of our revenue still comes from telecom industry clients.
Meanwhile in 2018 Thales acquired Gemalto, a $3 billion digital security firm with 15,000 employees. And Thales has put both Guavus and Gemalto in the same digital identity and security business unit, what they call their Analytics and IoT Systems (AIS) group.
| Sounds like Thales is very serious about being a digital systems integrator. But let’s switch now to the telecom fraud business of Guavus where I understand your biggest success has been in stopping data abuse through “tethering”. Can you give us a quick backgrounder on what tethering fraud is about and how it occurs? |
Kent McIntosh: Sure. Tethering fraud is wireless abuse, the unauthorized linking of a wireless device to a computer or smartphone to pump IP traffic through it. It’s basically a violation of the agreement the service provider has with its customer.
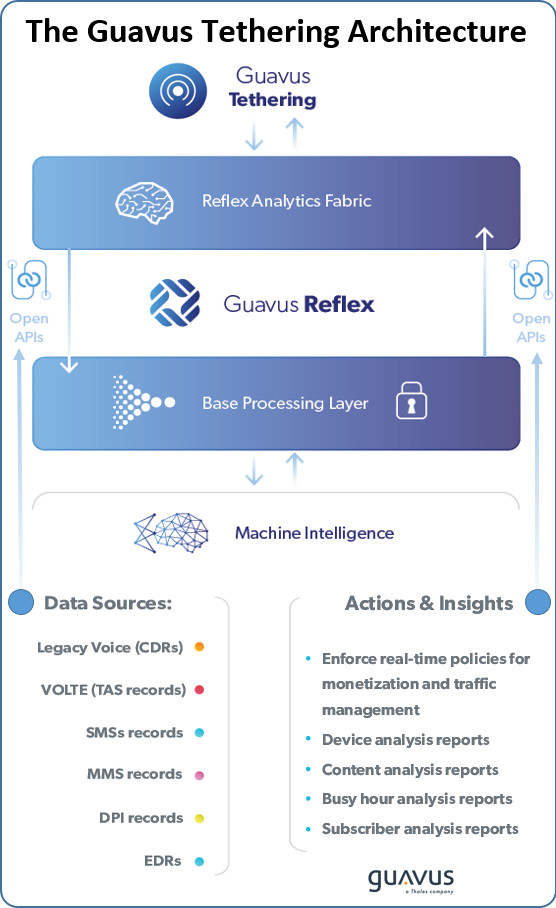
We combat the data abuse and tethering problem using our TetheringIQ fraud detection and prevention product.
Swapping out SIM cards is the main way fraudsters enable illegal tethering. For example, a fraud takes a SIM used in a high-capacity broadband device authorized for use in rural areas, and then deploys it in a device that enables, say, taxi drivers in a city to offer free wireless service to customers in their taxis.
We detect tethering fraud through geo-location and user ID restrictions, then we communicate with a policy management system that maintains a record of devices in the network and the proper SIM cards for each kind of device.
Now in the North American market, most mobile users have an all-you-can-eat data plan with a bandwidth ceiling. So what the service providers really need to know is: how much data is each SIM card generating from a tethered device and who’s doing the tethering? When you know that, you can use a closed-loop action to either block the usage or slow down the traffic when the customer’s contract limit is reached or an unauthorized user is tethering.
So Guavus performs tethering control by gathering data from various deep packet inspection (DPI) devices and probes, then does all the analytics.
Now the analysis of tethering is useful above-and-beyond the fraud control problems. For instance, tethering analysis is widely used by mobile operators to better clear up radio access network (RAN) bottlenecks and prevent other traffic congestion in areas of the network where excessive tethering usage is detected.
In all these tethering cases — fraudulent and otherwise — abusive tethering consumption leads to negative network effects and degraded quality-of-experience for a CSP’s customers. Ultimately, all of Guavus’ solutions improve the end-customer experience.
| So how do you actually go about detecting and analyzing fraudulent tethering? |
David Yates: Anytime a device is attached to a PC or phone, changes occur in the packet stream. So to detect tethering fraud associated with a particular SIM, you look at hop counts. Every time a packet goes through a relay device, a counter in the packet content records how many relay devices (hops) it has gone through. If the hop counter should change, you know tethering has occurred.
But blocking based on counting the number of hops is really only effective at stopping amateur fraudsters. The professional fraudsters — those who aim to push through huge volumes of data — take care to ensure that the hop count doesn’t change to an unexpected value.
So to catch the pros, Guavus digs deeper into the packet information — often using more complex Machine Learning-based analytics — to compute a high-probability score that a certain packet of conversation is from a tethering device.
Now thanks to the big OEM relationship we enjoy with Cisco, our tethering solution is pretty much universal across North America. And of course, we also serve operators worldwide who need to control tethering.
| OK then, your OEM business with Cisco is one good reason we haven’t heard much about Guavus in fraud detection. And why do you believe Cisco chose Guavus over the dozens of other capable analytics solution vendors? |
Kent McIntosh: I think it came down to our engineers’ deep telecom network understanding, which is exponentially more complex than the knowledge needed to perform website analytics. We know the kind of data telecom networks produce and the language that data speaks.
The second key skill set I’d say is our ability to manage huge data volumes. Telecom networks are among the biggest data producers in the world — collecting petabytes per day. In fact, we recently acquired a company called SQLstream, a real-time streaming analytics company and their technology allows us to perform more analytics at the network edge.
As data volumes grow, you need to perform as much analytics at the edge as possible and substantially reduce the volume transmitted-to and stored-in a centralized data lake or repository. And that’s where we think a distributed architecture becomes critical — and that’s what we have built, anticipating the needs of the operators in the 5G world.
| The Internet of Things (IoT) is another market Guavus pursues. What are some of the challenges there? |
David Yates: Dan, it’s important to understand how telecom service providers plan to serve the IoT market. In the industrial IoT market, the CSP merely offers low level connectivity to sensors and the integrator supplies the rest. But the market where telecoms are excited to play in is communications-rich IoT where real-time response, ID/fraud verification, and other controls are integral to the application.
An obvious telecom value-add is security. The IoT integration partner generally won’t have deep comms security knowledge, so here’s where an operator can deliver a wide umbrella of security/fraud protection for them.
There are IoT stories out there today about massive device spillover and lack of control. Here again, the operator can assist by offering its operational management to sort various streams of data and use-cases to determine which devices are vulnerable to fraud.
Now when you combine the security expertise of Gemalto and the tethering fraud control provided by Guavus, we think Thales is in a great position to help operators deliver that extra layer of protection for their IoT clients.
| How will Guavus serve the emerging 5G market? Where is analytics expertise needed in the next generation of mobile? |
Kent McIntosh: Well one area that’s critical to the success of 5G is delivering high quality data access. And by “high quality” I mean something much better than best effort (consumer-grade) internet access.
To deliver on that high-quality promise, operators need to excel in customer experience service management — figuring out what operational KPIs drive customer experience and relating those KPIs to fix issues in the network.
Operators are well aware of their knowledge gap here. It’s why NOC-to-SOC transformations (Network-Operations-Center to Service-Operations-Center) in the telecom industry have become urgent and that buzz word has emerged.
Guavus aims to provide a window on this customer experience — from both a device and network perspective. And we accomplish that by gathering data from probes and analyzing web content consumption, app usage stats, and location-specific metrics.
For instance, a number of our applications measure the customer experience. Then, by integrating our analytics with orchestration systems, operators can heal their network automatically by fixing the problems we identify.
The overall goal is to achieve a self-optimizing network. And that fits our tagline: “real-time insights, right-time decisions and closed-loop actions”. We pair visibility on inside network elements with our analysis of outside devices and subscribers. The whole idea is to help the operator make optimization decisions — either manually or through closed-loop automation.
| By the way, can’t the operators get a lot of this analytics data directly from, say, the RAN equipment suppliers like Ericsson, Huawei, and Nokia? |
David Yates: Yes, the RAN providers do provide such data. But the operators complain they need a third observer. Otherwise, they feel, it’s like asking the fox to guard the hen house. The truth is that the equipment vendor sometimes present results that are much rosier than the customers are actually reporting.
And, unlike those network infrastructure vendors, Guavus solutions are agnostic to the underlying equipment, so we can provide insights across an entire multi-vendor environment. Lastly, we don’t impose redundant data silos to serve our software solutions like those equipment suppliers. Guavus software sits atop an existing centralized data lake.
| David and Kent, thanks for this fine tutorial on how analytics is being applied to big data fraud and service management concerns. You’re in the thick of building solutions needed for IoT and 5G. |
Kent McIntosh:Well, Dan, the race is on to give operators a clearer view of customer (and machine) experience and to automate network healing. Remember, lots of these IoT experience problems are going to be machine driven, so operators will no longer have the economic luxury of hiring more staff in the NOC or call center to sort out problems.
In other words, analytics will become a big part of the ecosystem. And the fly-by-wire nature of 4G and especially 5G networks will make solving these problems quite a challenge. Applying AI to these operational issues will be another big step forward — in areas such as subscriber awareness, subscriber marketing, fraud prevention, and roaming and alarm management. These are areas we are really pushing right now.
And maybe the biggest trick of all is doing all these things efficiently. While operators are keen to deliver a higher quality customer experience, it needs to be done without unduly affecting top line profitability.
Copyright 2019 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum



