| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
June 2017
Stealth Test Calls: A Powerful New Weapon in the Fight to Block SIM Box Bypass

The two biggest toll call threats today are International Revenue Share Fraud (IRSF) and SIM box bypass. Yet these frauds call for very different detection strategies.
Here’s a playful analogy to show the contrast:
- IRSF fraud is like a focused attack by hungry bears who periodically find holes in your fence.
- SIM Box fraud is a sustained and omni-directional attack by an army of stinging ants.
Now passive Fraud Management Systems (FMSs) are ideal for blocking IRSF, but by themselves, they are a rather poor tool for detecting SIM Box fraud. Here’s why:
- SIM Box fraud exploits mass calling to any destination in a country. In IRSF, detection is simplified by searching blacklists and high-rate destinations around the globe. But in SIM box fraud, pinpointing the actual fraud route is far tougher. That’s because each attack is launched from a country’s vast pool of active mobile SIM cards — and those cards can number in the millions. Each individual SIM box call may be less profitable for the fraudster, but taken en masse, the total fraud-hit over time can be just as costly.
- A large bank of SIM cards can “fly under the radar” of detection. A passive FMS looks for call usage spikes by a particular SIM. Trouble is, fraudsters these days use versatile SIM servers that rotate the usage of SIM cards from on-line banks of thousands of SIMs. So the usage of any particular SIM card can be kept quite low.
OK, so what’s the key takeaway here? I think it’s this: to effectively block SIM Box fraud requires a dual defense. Passive FMS detection must be combined with active detection via test calls that probe the interconnect routes of SIM Box traffic.
One guy who’s intimately familiar with the tactics and technology needed to stop SIM box fraud is Kenneth Mouton, head of SIGOS’s Interconnect and Fraud division.
In our discussion, Kenneth updates us on the capabilities of Terminator, SIGOS’ hybrid test call and CDR profiling system. And in a major anti-fraud breakthrough, he explains SIGOS’ new stealth technology that is seeing great success in the fight against SIM box fraud.
| Dan Baker, Editor, Black Swan: Kenneth, we had our last extended discussion for TRI’s 2015 report on fraud control solutions. We’re now updating that study for 2017, so I’m eager to catch up and hear what SIGOS has been up to the past two years. |
Kenneth Mouton: Dan, we are still very much focused on interconnection fraud — and that fraud is moving way beyond SIM box fraud.
For instance, we have an automated solution to detect the refiling of CLIs which allows, say, an international operator to pretend it is a local operator within the European Union and thus enjoy a lower interconnect rate. And we’re also very active today in a relatively new area for us: SMS fraud.
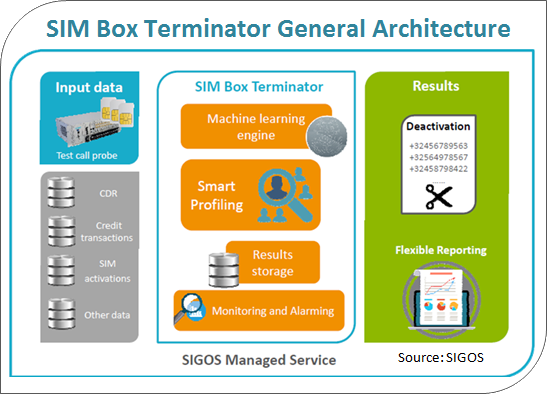
Our thrust in all these interconnect fraud areas is being driven by Terminator, our new hybrid fraud-fighting platform that combines test calls and CDR profiling. In the last two years, we have deployed Terminator in more than 10 countries.
| How are you applying the Terminator platform in fighting SIM Box bypass? |
Well, blocking SIM Box fraud is the reason we developed Terminator in the first place. You really can’t let your solution stand still in the SIM box area because the fraudsters are constantly improving their technical and human counter-measures.
But combining test calls and CDR profiling in one platform is a real boost because the faster you are at detecting and blocking SIM box fraud, the more you can prevent the fraudster from making money. Once an individual SIM card is used for 30 minutes or more, generally that becomes a very profitable threshold for the fraudster.
By the way, with our CDR profiling, we are really not competing in the revenue share fraud protection area where vendors like Subex, WeDo, and HP play. With Terminator, our CDR analysis is optimized for SIM box detection and the other interconnect frauds we track.
Now it’s one thing to merge test calls and CDR profiling, but what really allows Terminator to shine is its connection with SIGOS’s world-wide testing network that spans 200+ countries. This is the largest test call system in the world for fraud detection. And it puts great power into the hands of our investigators who work on one unified piece of software and have a globally automated test call system at their disposal. If a test call finds a SIM box, the system will automatically look up the CDR profile. If there’s a new antenna cell, it monitors that too.
Another point: our analysis today goes beyond CDR profiling. For example, we also look at the voucher and credit card transaction feeds to see when SIM cards are topped up. Activation data is invaluable as well because it tells you which SIM cards are bought and sold by each dealer.
We’ve also greatly improved the compute performance of our platform in the past two years.
Before, if you said China Mobile wants to use the SIGOS platform, we’d shy away from that business because we lacked the scale. But today, thanks to a major investment and excellent design done by the SIGOS team in Germany, we now have a fully scalable multi-server solution that is completely virtualized, meaning whether we use 100 servers or two servers inside, the system is optimized and the software looks the exact same to the user.
So, our performance constraints have gone away, and that’s important as we start to do trials in India where the number of subscribers on the network is huge.
Now I can’t say we’ve got the most fancy system in terms of big data and analytics: the system is still partially SQL-based. But we’ve added some new-fangled Facebook technology, RocksDB, to make it performant enough to serve the largest T1 operators.
| I recently wrote a white paper advocating regulators get more actively involved in SIM Box fraud control because, in many cases, the fraudsters pit one operator against another to enhance their illegal profits. |
Certainly working with regulators is now a big part of our business, especially in regions like Asia and Sub-Sahara Africa.
The regulators are keen on fraud control solutions to protect government tax revenue and to boost foreign currency inflow.
One of the largest customers is the regulator in Bangladesh. To be more precise, the mobile operators in Bangladesh are the ones who actually pay us although it’s the regulator who is strongly driving them to invest in our fraud control solutions.
In Bangladesh, the regulator has enacted strong laws that say: if SIGOS bans a SIM Box number and you don’t comply we will revoke your license.
While the punishment seems harsh, its policy is working to control the SIM box problem in that country. And the consequences of not responding quickly are costly. For example, if we notify an operator and it takes them 2 hours to block a SIM Box, that’s 2 hours of lost revenue and a decline in call quality. It all adds up very quickly.
So, the Bangladesh regulator is driving mobile operators to treat the SIM box problem in a professional way.
| OK, now that you’ve given us a refresh on how you’re combating SIM Box fraud these days, I’m eager to hear about your new stealth test call innovation. |
Great. To understand the value of our new stealth technique, it’s first worth reviewing why the test call numbers that we receive from our customers are vulnerable.
The key problem in classic test call SIM Box detection is that we always need to get test numbers from our customer, and they send us, say, 1,000 numbers to use. Here are the three key problems we run into:
- Internal Corruption
- Fraudster Detection of Test Call Numbers
- Detecting Non-Subscriber Behavior
We know that corruption and internal fraud happens in organizations around the world. Maybe this fraud is less prevalent in the US and Europe, but certainly there are places in Africa, Latin America, and Asia where it’s a daily occurrence.
We still experience many cases where we don’t find any SIM box fraud at all with our test call system, but then when we buy SIM cards on the street, we find that lots of fraud is occurring.
This happens because the fraudsters have bribed someone to get access to the SIGOS test numbers.
If we use, say, 1,000 test call numbers and make 20,000 calls to those numbers, we’ve established a certain pattern and the fraudsters have tools to detect those numbers by understanding the pattern of test calls.
For instance, a common way to find our test numbers is to let your SIM boxes get caught. If you have 1,000 SIM boxes and you know that SIGOS only has 100 test numbers in a certain country, then you just let your SIM cards be found, and that tells you that one of the calls that went through the SIM box before it was deactivated must have been a SIGOS call.
And the last problem with test numbers is that they are not real. There’s no real subscriber on the other end, and the fraudster can verify through call patterns which telephone numbers are not active versus ones that show normal calling behavior.
Once a number is verified as a real subscriber number, it’s whitelisted for sending fraudulent calls through the SIM box. However, when the fraudsters find a test number, its blacklisted, meaning they need to channel any calls to that number through a normal, legal route.
So, these three problems we’ve seen consistently over the past 10 years. However, we came up with a new stealth technology which is very fast and effective, and it is now also patented in many countries.
| OK, so how does your new stealth test call method work? |
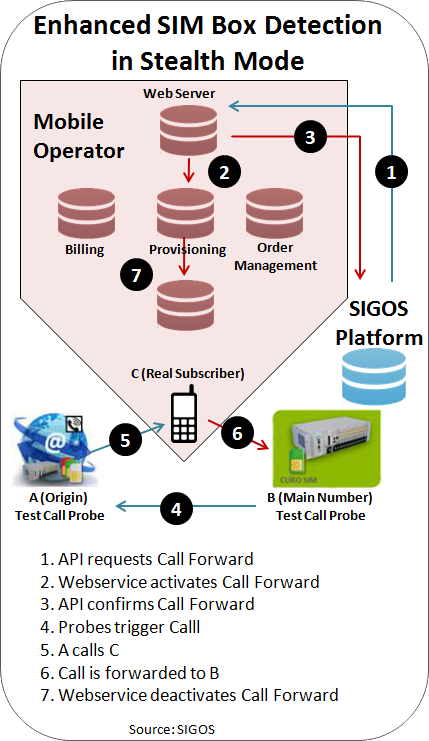
Well, we start by having our customers give us the phone numbers of all active subscribers. So, for instance, an operator might give us their 50 million active telephone numbers. And then when we make a test call, it is going to randomly pick one of those 50 million numbers.
We communicate with an API on the telecom’s end that’s connected to their provisioning system that requests the number be forwarded for 30 seconds.
When we get confirmation that the number is in call forwarding mode, we make the test call to detect a SIM box, after which the call forwarding is deactivated.
So, as you can see, this is a fully automated system that cannot be intercepted by internal fraud. It is not possible to detect because the SIM box fraudster or internal fraudster has no idea which of the 50 million numbers was used to do the test, and he cannot block all 50 million numbers from his SIM Box, there would be no traffic left.
Secondly, it’s invulnerable to counter-detection because if we have 50 million numbers, we can use a different number for each call. If they find those numbers, the next time we will make a call, we will use a different number.
And finally, these are real numbers with real profiles, so the whitelisting techniques cannot be used.
| Wow, it’s a beautiful invention. And I’m amused that it’s based on the same principle of hiding in a vast pool of numbers that the fraudsters use to avoid SIM detection in the first place. How widely is the solution deployed today? |
Well, so far we have this in the countries of Chad, Moldova, Guatemala, Congo, and Ghana. And everywhere we have installed it, the results are spectacular.
In Chad, for example, our first client who took the solution, we were finding approximately 10% SIM box prior to using the stealth technique. But once we went stealth, we discovered SIM box bypass was an astounding 90%.
The client was obviously thrilled at the results and the only downside is of course, that your telephone number could be call forwarded for 30 seconds every 10 or more years.
Of course, you should know you still can make outgoing calls; you can still browse the internet and send SMS etc. It’s only an incoming voice call that’s diverted.
In the U.S. or Western Europe, stealth mode might not be an option. But the rest of the world is open to such an advanced solution and that’s where most of SIM Box fraud is occurring. We think it’s a game changer — it’s definitely winning the hearts and minds of customers — that’s also why we patented it worldwide.
| What does the operator need to do to support your stealth mode? |
They need to set up a web service. We send them an HTTP request with the number to be call forwarded, and they have to develop a script on their provisioning system to do some checks on the number and if positive, submit it for call forwarding.
They are also responsible to deactivate the call forward after 30 seconds, and so the full responsibility and security is with the operator, not with us.
| A lot of operators will not have 50 million numbers. |
Well, even if we did one million test calls a year, then on average, your number would only be call forwarded once a year.
The key is it’s such a large set of numbers that the fraudster can’t black list the numbers.
It also reduces the work load at the customer, because you don’t have to fiddle anymore with all those test numbers. There’s a new API we need to monitor, but it’s definitely an improvement in performance and a long-term solution against SIM boxes actually.
| Thanks for this highly interesting briefing. And congratulations. Terminator and Stealth Test Calls are major contributions in the fight against interconnect fraud. |
Copyright 2017 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


