| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
November 2012
International Revenue Share Fraud: Are We Winning the Battle Against Telecom Pirates?

International Revenue Share Fraud (IRSF) is one of the telecom industry’s most enduring problems. Yet many of us who are familiar with IRSF have only a foggy notion of how it works and how operators around the globe are coping with the issue.
Well, here to give us a first class briefing on IRSF is a true international expert on the issue, Colin Yates, who only a few months ago left his post as the head of Fraud Management at the Vodafone Group to start a consulting practice. Our interview covers the bases: the origins of IRSF, typical fraud scenarios, efforts to get international cooperation on the issue, and the future outlook of IRSF.
| Dan Baker: Colin, international revenue share fraud is a well-known issue today, but the practice is actually not very old. |
Colin Yates Yes, Dan. It started on the internet and has gradually migrated into mobile and fixed line networks
It was around 2005 or 2006 when IRSF fraud termination in the Pacific Islands really accelerated as a fraud issue. New technology is what’s really opened up opportunities for fraudsters.
In particular, you can trace the rise in mobile fraud to the success of mobile marketing, particularly the ease of obtaining a Simcard for international roaming. Most of the fraud methods in those early days involved getting access to SIM cards and using them while roaming to call international revenue share numbers, knowing it would take 24 to 36 hours for those call records to get back to the home network.
In that window of opportunity, the fraudsters could dial as many IRSF numbers as they could before the home network became aware of the traffic and terminated the simcard.
As mobile phone technology progressed, we gave them the smartphone with the ability to make 6 simultaneous calls by utilizing the conference call facility on the handset. On your mobile handset, you can call a number, put it on hold, then call a second number, put it on hold, etc. So if the bad guys make 6 calls at once off of one SIM card, at $5 a minute, that’s a pretty nice income.
There were other features as well. International call forwarding was another boon to fraudsters. You could call forward a fraudulent simcard to an IRSF number in Somalia for example, make a local call into the forwarded device and have that automatically transferred to an IRSF number in Somalia, which could be repeated after each call connected.
| What are the trends in mobile generated IRSF? |
Over the last six or seven years, I would say IRSF has changed character, but the problem has not abated.
Back in 2005 or 2006 timeframes, it wasn’t unusual to hear about a fraudster armed with four SIM cards pulling in $100,000 of revenue over a weekend of calls. The more organized groups with 40 to 50 hijacked SIM cards could pull down several million $ over a weekend.
Then, about four years ago the GSM association approved a project to implement Near Real-Time Roaming Data Exchange (NRTRDE), allowing operators to get their hands on their international roaming call data much faster. That new process reduced that 24-36 hour time period between the fraud taking place and getting the roaming records at the home network. So NRTRDE was key to reducing the IRSF window to only 4 hours, which helped to take away many of the big fraud hits. However despite this initiative, if you have a Fraudster operating with a cluster of 30 or 40 cards with a number of ‘Mules’ making calls at the same time, you can still do plenty of damage -- even in 4 hours, this level of activity can result in losses in the $50,000 to $100,000 range.
| Who are the operators getting the traffic? |
A lot of the calls were related to premium rate services around the world. Once again, technology advancements made it easier for the fraudsters to inflate traffic into high value premium rate numbers. There are now software based techniques to block international premium rate numbers from being completed, which helps operators reduce this risk.
Why Certain Countries are IRSF Destinations
To get around the issue of blocked international premium rate numbers, fraudsters have picked on countries that have high interconnect or termination rates. If I made a call from the UK into AT&T for example, the international call rate might be 2 cents a minute. That’s the charge AT&T will bill BT for terminating the call in the U.S.
But in countries such as Cook Island and many other small countries in the Pacific, their international termination rate is more like 60 cents a minute. This high termination fee is a magnet to fraudsters. It means the fraudster can make money in a much tighter window.
A common issue now being experienced by the industry is number misappropriation or number hijacking. For example, a call from the UK to a Pacific Island country code may never get there. It will be stopped somewhere in the call routing chain and rerouted to an information line, chat line, fortune telling, etc, or simply terminated onto a ringing or other tone
Fraud management teams around the world are closely monitoring the fraud calling destinations and as fraud numbers become known, may block these numbers at their switches Unfortunately , the precise numbers being exploited change on a daily basis and it’s a constant challenge to keep up with these new numbers.
| Colin, why can’t the operator being socked with the huge fraud bill refuse payment? |
I know the stop payment option on known fraudulent numbers seems like a good strategy and an obvious way to go. Unfortunately, we tried doing that believing that if we could stop the money flow, we would disrupt the fraudster’s business case, but we failed. The problem is, to do that, you need cooperation from every operator in the call transit chain. The fraudulent calls may pass through 6 or 7 operators to get to their termination point and getting agreement from that many operators is very difficult. Now you might be able to get 4 out of 5 operators to cooperate, but invariably there’s one operator who won’t give you the routing information you need to identify who they routed the call to.
Bound by International Agreements
In essence, carriers are bound by international agreements for roaming and interconnect payments. And as you might expect, the terms of these agreements were made long before IRSF came into existence. The basic GSMA roaming agreement for example, which is bilaterally agreed between two operators says that the originating operator must pay for all calls originating from his network — whether it is fraud or not.
It’s a big controversy and I personally feel that the originating carrier has the right to know how his call was routed.
When it comes to payment time, each operator just pays the operator he passed the calls off to, with no knowledge who is next in that payment chain.
The Body of European Regulators (BEREC) are beginning to appreciate this issue more, and are currently talking about how to make it easier for operators to extract the details of exact routing of every call that may have been made fraudulently. That would be a very big help indeed. It will help operators ultimately to stop the money, which will reduce the problem, but the fraudsters will simply move onto something else.
| What’s the impact of IRSF on all-IP networks and LTE? |
More and more business customers are now moving to IP-PBXs and this can actually make it easier for technology savvy fraudsters to penetrate and use this access for IRSF. However the vulnerabilities of some traditional PBX’s, which have allowed fraudsters easy access to networks for the past 10 years or so, are still cropping up on a weekly basis.
And the people involved are more sophisticated now: it’s organized crime, people who can afford to hire those with the knowledge to penetrate any controls put in place.
As the industry works on LTE and next generation networks and making sure we have effective security controls around that, we can guarantee that groups of fraudsters are also working hard to break those defenses.
I have no doubt that fraudsters will find ways around every obstacle we put in front of them. They always do. This is not their hobby, it is their business.
Going back six or seven years, most of the IRS fraud was called through fraudulent SIMs that were roaming. But now we’re seeing a lot more through PBXs. For instance, there are some groups based in the Philippines who are continually dialing out to nations of the world looking for a PBX that they can hack. This could be through an insecure DISA line, a maintenance port or any other vulnerable entry point where they can gain access to an outgoing trunk. They then contact their organized crime associates who pay them for that information and then use the access it provides to make IRSF calls.
Today, many in the industry believe that the PBX has become more common as an IRSF enabler than the mobile phone with fraudulent SIMs.
| Are we making any headway as far as industry cooperation in IRSF? |
Yes, various industry groups maintain a database of the latest fraudulent numbers. A lot of information sharing goes on between operators who accept that fraud management is a non-competitive area of the business. If a range of fraudulent numbers is found in say, a small African country, these will get reported through industry forums such as the GSM Association or the Communications Fraud Control Association, and a hot list is generated.
This is one area where Xintec offers a viable solution to keep the hot lists updated. That helps you identify the known numbers being used for fraud and these are being updated on a daily basis. Unfortunately someone has to have a fraud hit to find out what these new numbers being used are.
| What’s being done to alleviate the issues in the Pacific Islands? |
Well, the Pacific Island operators are very concerned at the impact this number hijacking is having on their customers, their communities and their reputation with other international operators. This is something which is out of their control and really, they are also victims of this fraud. Some of these islands only have a customer base of 2,000 or so people and some operators around the world are blocking the whole range in an Island from receiving calls because of a perceived fraud risk. So if an islands number range is hijacked, it may take a couple of days before the routing returns to normal.
Typically we know the country codes where revenue share fraud is taking place, so Fraud Detection System thresholds on calls to those countries will to try to identify them early.
I’ve been recently working with the Pacific Island Telecom Association. Because most islands have such high termination rates, they are very popular for revenue share. The majority of Pacific Islands won’t entertain relationships with any of the number aggregators offering the numbers.
The fraudsters will likely have a relationship with a dishonest or unscrupulous operator which could be a traditional or Voice over IP operator who will terminate the traffic destined for those islands outside that country. We call it short-stopping. They will stop the call before it gets to the correct country, so it can be terminated into another country onto a voice mail system, information line or recorded message. That’s instead of forwarding the call through the approved routing for termination in the correct country. Because it’s a Pacific country code, it’s still billed at around 60 cents a minute instead of a few cents if the real termination rate for the country where it actually terminates was used..
| This is highly interesting stuff, Colin. But I’m still confused about how IRSF is pulled off. What’s the role of the various parities in the IRSF transaction? And how do some of these fraudsters get into the business in the first place. |
Dan, IRSF scenarios can be very confusing and the fraudsters have an interest in keeping it that way to cover their tracks. The following diagram and explanation shows a typical IRSF scenario using mobile roaming.
International Revenue Share Fraud
Mobile Roaming Scenario
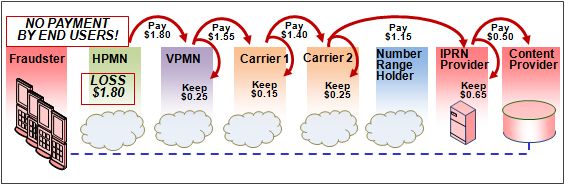
The flow of the IRSF case above is as follows:
- Fraudster obtains Simcards (fraudulently) from the HPMN (Home Network) and takes these across an international border to a VPMN (Visited Network) and calls IRS numbers
- HPMN receives no payment for these calls but must pay the VPMN for their origination
- VPMN must then pay Carrier 1 to whom he passed the call. In turn, Carrier 1 must pay Carrier 2, and so on, until the payment reaches the IPRN (International Premium Rate Network) provider. The IPRN will, in turn pay Content Provider for supplying its content and keeping the call minutes as long as possible to increase the billing charge.
- Content Provider will have a relationship with Fraudster who shares the proceeds. Often the IPRN provider and the content provider are the same person.
- In this case the IPRN provider will have leased or purchased number ranges from the Number Range Holder
How Fraudsters Advertise Themselves
Frankly, IRSF is a fairly easy business to get into. Do a Google search on international premium numbers and you’ll see how many International Number Aggregators are advertising for business. It’s all there: a sign up form and a registration page detailing how much they pay you for generating traffic to their numbers, which in some cases may be hijacked ranges. What they are looking for is companies and individuals who are willing to drive or inflate traffic to those phone numbers. And the numbers are often provided, and payments settled on a 15 to 30 day basis.
Between 2009 and 2012, the number of sites has increased 140%. So there are more fraud groups who are realizing the monetary benefits of this fraud. In short, the number of fraudsters is increasing.
It is important to emphasize that not all revenue share number aggregators are fraudsters. There are legitimate operations out there who are offering genuine terminations into the correct country for various information services, voting lines etc. However my own analysis of the huge increase in the number of sites offering these numbers would indicate that many of these sites are either advertising numbers without the authority or knowledge of the number range holder, terminating the numbers against ITU recommendations, or not performing any due diligence on those they are supplying the numbers to.
The fraudsters live and operate all around the world. There are many in Europe, the Middle East and Africa and South America.
The IRSF Number Providers
The number aggregators involved in this are generally not licensed telecom operators at all. I guess the closest description would be to call them international revenue share number providers. They are not really premium rate number providers as most of the numbers they are terminating calls on are not classified as premium rate under the ITU definitions, but simply assigned or unassigned numbers into a country which attracts a high termination rate. But they are not licensed by any government or agency nor do they report to any regulatory authority.
They are offering numbers in countries where they have no relationship, particularly some in the Pacific Islands. The operators in those countries have no idea that their numbers are being compromised until they are advised by another operator, or receive complaints from their customers.
There are however many telecom operators around the world who are prepared to offer their numbers to these number aggregators either on a lease or revenue share basis.
Why It’s Hard to Detect and Reconstruct IRSF Cases
It’s often difficult to get law enforcement involved in investigating IRSF because generally it’s so complex as it crosses so many international boundaries. A typical example could be where you have a SIM card from the UK being obtained by a fraudster using a stolen identity and shipped to another fraudster in Spain to make calls to revenue share numbers in Somalia, with the fraudulent proceeds being transferred to a criminal gang in Pakistan. So in that case you’ve got three international boundaries to sort out with fraudsters operating in 3 or 4 different jurisdictions. So the police often throw up their hands citing the jurisdictional issues and uncertainty of where the actual fraud occurred. .
You need two sides to make it work. At the terminating end, the idea is to keep the person on the line as long as possible to drive up the fraudulent revenue. It may be just a voice recording asking you to hold. Or they might say, “You’ve just won a prize. Please wait for more details”. Other fraudsters will just have a reoccurring message to keep the caller on the line. They might keep a call open for close to 60 minutes.
Of course, the person calling is usually a fraudster as well. In some cases, they will terminate the call at say 55 to 57 minutes knowing a number of fraud management systems are programmed to alert for calls that are an hour or longer to a high risk destination.
So there are two scenarios. You have some calls that are automatically generated. And then consumers are calling the numbers. And there are cases where consumers are looking for an opportunity to make some money. In the end someone has to pay to terminate these calls, but if there is no customer to bill because the connection is fraudulent then the originating operator has to pay and carry that loss.
| Colin, in your new fraud management consulting firm you struck up a relationship with Xintec. |
Yes, when I left my job as Group Head of Fraud Management at Vodafone in July 2012, Xintec offered me the opportunity to become their consultant. When I was first getting into the fraud management business, I started talking about the need for the industry to have a lower cost entry level into fraud management systems for smaller operators.
Their solutions have become very successful for tier 2 or 3 operators. With Xintec, operators have the opportunity to do 80% of their fraud detection without spending a million dollars. It’s a good business model.
| At Vodafone, couldn’t you use the group purchased fraud solution for the many small operators that Vodafone has in its group? |
Actually, Vodafone was moving towards that model — a shared service centre environment with one or two centralized fraud management systems that collect core records from other countries.
But privacy issues were just one roadblock. It’s hard to get the authority for local operators to send their call records to another country. In the end, this is why we started implementing Xintec solutions into some of our smaller operators. It ended up being a lot more cost effective as an interim approach until the day when they can establish a centrally managed system.
I think there’s huge potential for group operators to move to a shared fraud management model, and the trend towards cloud-based solutions will probably speed that along. As I’ve said, political and data sharing issues are blocking the move right now and these may take a long time to resolve.
| Colin, thanks much for this detailed and highly interesting briefing on IRSF. What’s your crystal ball tell you about the future? |
Thanks, Dan. IRSF is a huge problem that the industry finds difficult to manage. Unless we start getting some localized legislation in countries to stop the money flow, it will continue to be difficult to manage. Stop the money and you stop the problem.
In my view, the operator shouldn’t be paying money when they know that at the end of the payment chain, a percentage of this is going to get into the hands of fraudsters. In my view, this money is the proceeds of crime and payment could constitute money laundering. It is not possible to just pay the legitimate carriers involved in transiting these calls, as in the absence of any transparency in the call routing, it is not possible to identify where in that call routing the call is being terminated.
Copyright 2012 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
cSwans of a Feather
- Deep Fraud Investigations: Mavenir and the Role of Machine Learning in IRSF Control — interview with Ilia Abramov & Marie Casey — Machine Learning-based fraud protection promises an answer to blocking fraud with precision, especially in roaming and nextgen mobile networks. An ML champion discusses unusual and interesting fraud schemes uncovered by deep investigations.
- Safety in Numbers and NRTRDE: Syniverse’s Strategy to Constantly Enrich Its Mobile Fraud Intelligence — interview with James Stewart — A discussion on NRTRDE, the Near Real Time Roaming Data Exchange, the complexity of the roaming settlement process, and the fraud challenges mobile operators face as their subscribers roam.
- Global Interconnect Specialist iconectiv Ramps up its Fraud & Identity Solutions in Bypass & A2P Messaging — interview with Bojan Andelkovic — Today’s IRSF, SIM Box, and SMS A2P frauds call for coordinated and broadly conceived FM programs. A leading interconnect specialist explains the benefits of its managed services approach.
- A Real-Time Packet-Based Solution to Detect & Block any Hijacked OTT Call — interview with Paul David & Andy Gent — Two veterans of the SIM Box call bypass wars describe a new solution for stopping OTT bypass. Get vital intel on the call hijacking of VIBER and other OTTs. Learn why the revenue threat to roaming is as serious as it is to international calls.
- Protecting the Roaming Cash Cow: Using a Global Test Network for LTE Deployments & Beyond — interview with Florian Leeder — International is a premium service that operators must ensure the roaming business is reliable and optimized. This article makes the case for a global roaming test service. It explains the problems operators face in contracting with roaming partners, maintaining quality, and rolling out LTE.
- Recruiting Smartphone Users as Partners in Telecom Fraud & Security Control — by Tal Eisner — Premium Rate Service (PRS) fraud and spyware on a mobile phone can ruin an operator’s relationship with a subscriber. The attacker uses malware to automatically generate phone calls, SMSs and data sessions to high cost (premium) phone numbers. This article discusses a new crowd sourcing mobile app that addresses the problem and helps operators better manage the threat.
- Roaming — if Managed Correctly -- Can Be a Spark to Revenues — by Brian Silvestri — Major analyst firms are predicting that roaming revenues will almost double in five years. What’s more, roaming remains at the pivot point of Wireless Carrier strategy. Drawing lessons from the incredible rise of AT&T’s Digital One Rate Plan, this article points to future challengtes and raises key questions about how mobile operators will ultimately come to terms with smartphone market profitability, service quality, and data roaming.
- International Revenue Share Fraud: Are We Winning the Battle Against Telecom Pirates? — interview with Colin Yates — International Revenue Share Fraud (IRSF) is one of the telecom industry’s most enduring problems. Yet many of us have only a foggy notion of how IRSF works and how operators around the globe are coping with the issue. This interview covers the bases: the origins of IRSF, typical fraud scenarios, efforts to get international cooperation on the issue, and the future outlook of IRSF.
- Roaming Fraud: The Importance of Real-Time Data Exchange and Analysis — interview with James Stewart — The Near Real Time Roaming Data Exchange (NRTRDE) is a GSM standard allowing operators to gain fast access to the roaming records of service providers half way around the world. The article explains how 65 carriers are using this data to combat fraud through a service bureau. Learn about the dangers of international roaming fraud and the value a roaming service bureau brings to the table.
Related Articles
- Tokopedia, Indonesia’s E-Commerce King, Partners with 11 Million Merchants; Adopts Multi-Cloud to Drive Innovation — interview with Warren Aw & Ryan de Melo — Indonesia’s Tokopedia, founded in 2009, has grown to become one of world’s leading e-commerce players. Read about its success, technology direction, and multi-cloud connectivity adoption.
- Bridge Alliance: Knocking Down Regional & Mobile Connectivity Barriers so Connected Car Markets Get Rolling in Asia — interview with Kwee Kchwee — The CEO of an Asian consortium of mobile operators explains how they help simplify and harmonize their members‘ operations in support of multi-national corporations. This integration is enabling two huge industries to come together in Asia: auto manufacturing and telco.
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw — Network as a Service, powered by Software Defined Networks, are a faster, more agile, and more partner-friendly way of making data global connections. A leading NaaS provider explains the benefits for cloud apps, enterprise IT, and IoT.
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price — A leading wholesale executive explains the business challenges of the current global IoT scene as it spans many spheres: technical, political, marketing, and enterprise customer value creation.
- Senet’s Cloud & Shared Gateways Drive LoRaWAN IoT Adoption for Enterprise Businesses, Smart Cities & Telecoms — interview with Bruce Chatterley — An IoT netowork pioneer explains how LoRaWAN tech fits in the larger IoT ecosystem. He gives use case examples, describes deployment restraints/costs, and shows how partnering, gateway sharing, and flexible deployment options are stimulating growth.
- ARM Data Center Software’s Cloud-Based Network Inventory Links Network, Operations, Billing, Sales & CRM to One Database — interview with Joe McDermott & Frank McDermott — A firm offering a cloud-based network inventory system explains the virtues of: a single underlying database, flexible conversions, task-checking workflow, new software business models, views that identify stranded assets, and connecting to Microsoft’s cloud platform.
- Pure Play NFV: Lessons Learned from Masergy’s Virtual Deployment for a Global Enterprise — interview with Prayson Pate — NFV is just getting off the ground, but one cloud provider to enterprises making a stir in virtual technology waters is Masergy. Here are lessons learned from Masergy’s recent global deployment using a NFV pure play software approach.
- The Digital Enabler: A Charging, Self-Care & Marketing Platform at the Core of the Mobile Business — interview with Jennifer Kyriakakis — The digital enabler is a central platform that ties together charging, self-care, and marketing. The article explains why leading operators consider digital enablers pivotal to their digital strategies.
- Delivering Service Assurance Excellence at a Reduced Operating Cost — interview with Gregg Hara — The great diversity and complexity of today’s networks make service assurance a big challenge. But advances in off-the-shelf software now permit the configuring and visualizing of services across multiple technologies on a modest operating budget.
- Are Cloud-Based Call Centers the Next Hot Product for the SMB Market? — interview with Doron Dovrat — Quality customer service can improve a company’s corporate identity and drive business growth. But many SMBs are priced out of acquiring modern call center technology. This article explains the benefits of affordable and flexible cloud-based call centers.
- Flexing the OSS & Network to Support the Digital Ecosystem — interview with Ken Dilbeck — The need for telecoms to support a broader digital ecosystem requires an enormous change to OSS infrastructures and the way networks are being managed. This interview sheds light on these challenges.
- Crossing the Rubicon: Is it Time for Tier Ones to Move to a Real-Time Analytics BSS? — interview with Andy Tiller — Will tier one operators continue to maintain their quilt works of legacy and adjunct platforms — or will they radically transform their BSS architecture into a new system designed to address the new telecom era? An advocate for radical transformation discusses: real-time analytics, billing for enterprises, partnering mashups, and on-going transformation work at Telenor.
- Paradigm Shift in OSS Software: Network Topology Views via Enterprise-Search — interview with Benedict Enweani — Enterprise-search is a wildly successful technology on the web, yet its influence has not yet rippled to the IT main stream. But now a large Middle Eastern operator has deployed a major service assurance application using enterprise-search. The interview discusses this multi-dimensional topology solution and compares it to traditional network inventory.
- The Multi-Vendor MPLS: Enabling Tier 2 and 3 Telecoms to Offer World-Class Networks to SMBs — interview with Prabhu Ramachandran — MPLS is a networking technology that has caught fire in the last decade. Yet the complexity of MPLS has relegated to being mostly a large carrier solution. Now a developer of a multi-vendor MPLS solutions explains why the next wave of MPLS adoption will come from tier 2/3 carriers supporting SMB customers.
- Enabling Telecoms & Utilities to Adapt to the Winds of Business Change — interview with Kirill Rechter — Billing is in the midst of momentous change. Its value is no longer just around delivering multi-play services or sophisticated rating. In this article you’ll learn how a billing/CRM supplier has adapted to the times by offering deeper value around the larger business issues of its telecom and utility clients.
- Driving Customer Care Results & Cost Savings from Big Data Facts — interview with Brian Jurutka — Mobile broadband and today’s dizzying array of app and network technology present a big challenge to customer care. In fact, care agents have a hard time staying one step ahead of customers who call to report problems. But network analytics comes to the rescue with advanced mobile handset troubleshooting and an ability to put greater intelligence at the fingertips of highly trained reps.
- Hadoop and M2M Meet Device and Network Management Systems — interview with Eric Wegner — Telecom big-data in networks is more than customer experience managment: it’s also about M2M plus network and element management systems. This interview discusses the explosion in machine-to-machine devices, the virtues and drawbacks of Hadoop, and the network impact of shrink-wrapped search.
- The Data Center & Cloud Infrastructure Boom: Is Your Sales/Engineering Team Equipped to Win? — by Dan Baker — The build-out of enterprise clouds and data centers is a golden opportunity for systems integrators, carriers, and cloud providers. But the firms who win this business will have sales and engineering teams who can drive an effective and streamlined requirements-to-design-to-order process. This white paper points to a solution — a collaborative solution designs system — and explains 8 key capabilities of an ideal platform.
- Big Data: Is it Ready for Prime Time in Customer Experience Management? — interview with Thomas Sutter — Customer experience management is one of the most challenging of OSS domains and some suppliers are touting “big data” solutions as the silver bullet for CEM upgrades and consolidation. This interview challenges the readiness of big data soluions to tackle OSS issues and deliver the cost savings. The article also provides advice on managing technology risks, software vendor partnering, and the strategies of different OSS suppliers.
- Calculated Risk: The Race to Deliver the Next Generation of LTE Service Management — interview with Edoardo Rizzi — LTE and the emerging heterogeneous networks are likely to shake up the service management and customer experience management worlds. Learn about the many new network management challenges LTE presents, and how a small OSS software firm aims to beat the big established players to market with a bold new technology and strategy.
- Decom Dilemma: Why Tearing Down Networks is Often Harder than Deploying Them — interview with Dan Hays — For every new 4G LTE and IP-based infrastructure deployed, there typically a legacy network that’s been rendered obsolete and needs to be decommissioned. This article takes you through the many complexities of network decom, such as facilities planning, site lease terminations, green-safe equipment disposal, and tax relief programs.
- Migration Success or Migraine Headache: Why Upfront Planning is Key to Network Decom — interview with Ron Angner — Shutting down old networks and migrating customers to new ones is among the most challenging activities a network operators does today. This article provides advice on the many network issues surrounding migration and decommissioning. Topics discussed include inventory reconciliation, LEC/CLEC coordination, and protection of customers in the midst of projects that require great program management skills.
- Navigating the Telecom Solutions Wilderness: Advice from Some Veteran Mountaineers — interview with Al Brisard — Telecom solutions vendors struggle mightily to position their solutions and figure out what to offer next in a market where there’s considerable product and service crossover. In this article, a veteran order management specialist firm lays out its strategy for mixing deep-bench functional expertise with process consulting, analytics, and custom API development.
- Will Telecoms Sink Under the Weight of their Bloated and Out-of-Control Product Stacks? — interview with Simon Muderack — Telecoms pay daily for their lack of product integration as they constantly reinvent product wheels, lose customer intelligence, and waste time/money. This article makes the case of an enterprise product catalog. Drawing on central catalog cases at a few Tier 1 operators, the article explains the benefits: reducing billing and provisioning costs, promoting product reuse, and smoothing operations.
- Virtual Operator Life: Enabling Multi-Level Resellers Through an Active Product Catalog — interview with Rob Hill — The value of product distribution via virtual operators is immense. They enable a carrier to sell to markets it cannot profitably serve directly. Yet the need for greater reseller flexibility in the bundling and pricing of increasingly complex IP and cloud services is now a major channel barrier. This article explains what’s behind an innovative product catalog solution that doubles as a service creation environment for resellers in multiple tiers.
- Telecom Blocking & Tackling: Executing the Fundamentals of the Order-to-Bill Process — interview with Ron Angner — Just as football teams need to be good at the basics of blocking and tackling, telecoms need to excel at their own fundamental skillset: the order-to-cash process. In this article, a leading consulting firm explains its methodology for taking operators on the path towards order-to-cash excellence. Issues discussed include: provisioning intervals; standardization and simplicity; the transition from legacy to improved process; and the major role that industry metrics play.
- Wireline Act IV, Scene II: Packaging Network & SaaS Services Together to Serve SMBs — by John Frame — As revenue from telephony services has steadily declined, fixed network operators have scrambled to support VoIP, enhanced IP services, and now cloud applications. This shift has also brought challenges to the provisioning software vendors who support the operators. In this interview, a leading supplier explains how it’s transforming from plain ol‘ OSS software provider to packager of on-net and SaaS solutions from an array of third party cloud providers.
- Telecom Merger Juggling Act: How to Convert the Back Office and Keep Customers and Investors Happy at the Same Time — interview with Curtis Mills — Billing and OSS conversions as the result of a merger are a risky activity as evidenced by famous cases at Fairpoint and Hawaiian Telcom. This article offers advice on how to head off problems by monitoring key operations checkpoints, asking the right questions, and leading with a proven conversion methodology.
- Is Order Management a Provisioning System or Your Best Salesperson? — by John Konczal — Order management as a differentiator is a very new concept to many CSP people, but it’s become a very real sales booster in many industries. Using electronics retailer BestBuy as an example, the article points to several innovations that can — and are — being applied by CSPs today. The article concludes with 8 key questions an operator should ask to measure advanced order management progress.
- NEC Takes the Telecom Cloud from PowerPoint to Live Customers — interview with Shinya Kukita — In the cloud computing world, it’s a long road from technology success to telecom busness opportunity. But this story about how NEC and Telefonica are partnering to offer cloud services to small and medium enterprises shows the experience of early cloud adoption. Issues discussed in the article include: customer types, cloud application varieties, geographic region acceptance, and selling challenges.
- Billing As Enabler for the Next Killer Business Model — interview with Scott Swartz — Facebook, cloud services, and Google Ads are examples of innovative business models that demand unique or non-standard billing techniques. The article shows how flexible, change-on-the-fly, and metadata-driven billing architectures are enabling CSPs to offer truly ground breaking services.
- Real-Time Provisioning of SIM Cards: A Boon to GSM Operators — interview with Simo Isomaki — Software-controlled SIM card configuration is revolutionizing the activation of GSM phones. The article explains how dynamic SIM management decouples the selection of numbers/services and delivers new opportunities to market during the customer acquisition and intial provisoining phase.
- A Cynic Converted: IN/Prepaid Platforms Are Now Pretty Cool — interview with Grant Lenahan — Service delivery platforms born in the IN era are often painted as inflexible and expensive to maintain. Learn how modern SDPs with protocol mediation, high availability, and flexible Service Creation Environments are delivering value for operators such as Brazil’s Oi.
- Achieving Revenue Maximization in the Telecom Contact Center — interview with Robert Lamb — Optimizing the contact center offers one of the greatest returns on investment for a CSP. The director of AT&T’s contact center services business explains how telecoms can strike an “artful balance” between contact center investment and cost savings. The discussion draws from AT&T’s consulting with world class customers like Ford, Dell, Discover Financial, DISH Network, and General Motors.
- Mobile Broadband: The Customer Service Assurance Challenge — interview with Michele Campriani — iPhone and Android traffic is surging but operators struggle with network congestion and dropping ARPUs. The answer? Direct resources and service quality measures to ensure VIPs are indeed getting the quality they expect. Using real-life examples that cut to the chase of technical complexities, this article explains the chief causes of service quality degradation and describes efficient ways to deal with the problem.
- Telco-in-a-Box: Are Telecoms Back in the B/OSS Business? — interview with Jim Dunlap — Most telecoms have long since folded their merchant B/OSS software/services businesses. But now Cycle30, a subsidiary of Alaskan operator GCI, is offering a order-to-cash managed service for other operators and utilities. The article discusses the company’s unique business model and contrasts it with billing service bureau and licensed software approaches.
- Bricks, Mortar & Well-Trained Reps Make a Comeback in Customer Management — interview with Scott Kohlman — Greater industry competition, service complexity, and employee turnover have raised the bar in the customer support. Indeed, complex services are putting an emphasis on quality care interactions in the store, on the web, and through the call center. In this article you’ll learn about innovations in CRM, multi-tabbed agent portals, call center agent training, customer treatment philosophies, and the impact of self-service.
- 21st Century Order Management: The Cross-Channel Sales Conversation — by John Konczal — Selling a mobile service is generally not a one-and-done transaction. It often involves several interactions — across the web, call center, store, and even kiosks. This article explains the power of a “cross-channel hub” which sits above all sales channels, interacts with them all, and allows a CSP to keep the sales conversation moving forward seamlessly.
- Building a B/OSS Business Through Common Sense Customer Service — by David West — Delivering customer service excellence doesn‘t require mastering some secret technique. The premise of this article is that plain dealing with customers and employees is all that’s needed for a winning formula. The argument is spelling out in a simple 4 step methodology along with some practical examples.

