| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
January 2023
Registered Caller: A Centralized Registry Service to Collect, Vet and Send Enterprise STIR/SHAKEN and Rich Call Data to Consumers

STIR/SHAKEN is a now widely-adopted protocol enabling telecoms to feed calling party attestation info to consumers when they receive a call from businesses and organizations of all types and sizes.
First launched by the large U.S. telcos in early 2020, STIR/SHAKEN is helping reduce illegal telemarketing and spam calls. The protocol is now adopted by more than 400 telcos of roughly 1,500 in America overall.
STIR/SHAKEN is also an important tool for restoring consumer trust in answering phone calls. Today, that B-to-C trust has deeply eroded. One indicator: phone calls from legitimate enterprises — such as a consumer’s bank, pharmacist, and doctor — are routinely NOT answered by consumers.
So now, after two years in operation, has STIR/SHAKEN actually made a difference? Well, one positive indicator that it has comes from the FTC’s Consumer Sentinel Databook which yearly tracks all kinds of commercial fraud and abuse of U.S. consumers.
The FTC’s 2021 Databook shows the number of consumers complaining about “unwanted telemarketing calls or robocalls” dropped 50% — from 300,000 monthly complaints in 2019 to only 150,000 monthly in 2020.
Is that progress? You bet it is, but the high 150,000 monthly telemarketing complaints in 2020 shows we still have a long way to go.
But regardless of the potential for STIR/SHAKEN curbing illegal telemarketing and spam calls today, we should be excited about STIR/SHAKEN’s progress for one simple reason:
Large telcos have implemented STIR/SHAKEN so enterprises can convey their authenticated caller IDs to consumers.
Now as you well know, telcos are deeply reluctant to adopt programs that require collaborating with competitors. But STIR/SHAKEN has cleared that massive hurdle in less than two years! So now the stage is set for widespread adoption by U.S. enterprises.
But exactly how will STIR/SHAKEN evolve to create better communication between enterprises and consumers?
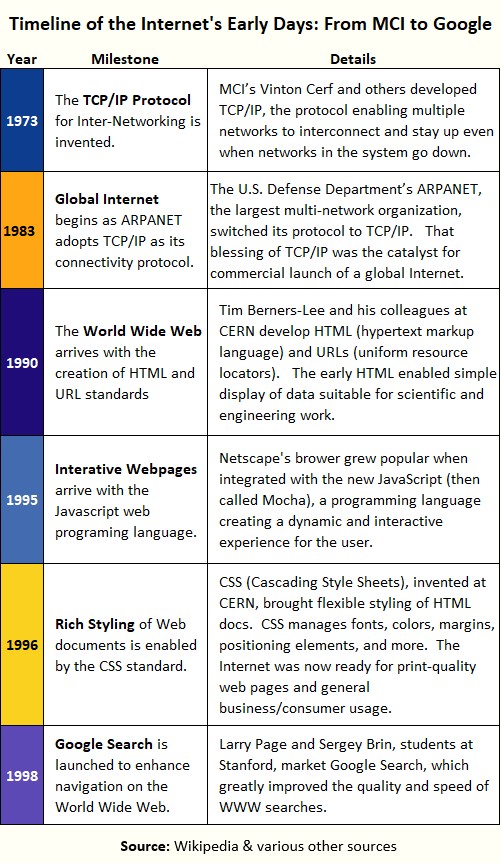
Well, consider how the Internet evolved. The Internet was basically born in 1983 when the U.S. government’s ARPANET (the largest inter-networking system of its time) chose TCP/IP as its universal network connectivity standard — and that led the way to TCP/IP adoption across big network users.
But TCP/IP connectivity, by itself, wasn’t enough to drive a huge mass market because the Internet lacked a “common language” or methodology to exploit that connectivity.
So the Internet languished for 7 years until a team at CERN led by Tim Berners-Lee introduced something called HTML, which, of course, is the lynchpin for the World Wide Web. The rest is history.
So what “common language” or industry-adopted methodology will enable STIR/SHAKEN to evolve to its next level of usefulness? Well, that’s the subject of this interview story.
We are pleased to welcome two key leaders shaping STIR/SHAKEN’s future. They are George Cray — Senior Vice President-Information Solution Products & Services at iconectiv, and Tom Sawanobori, the CTO of CTIA.
George and Tom explain why iconectiv and CTIA have teamed up to drive adoption of Registered Caller™, a new, central cloud service for enterprise vetting and validation to leverage STIR/SHAKEN info for telecoms in the U.S. market.
Registered Caller performs many tasks and enables new capabilities — as they’ll explain — but it essentially standardizes how enterprises will convey their authenticated caller ID and other pre-call info to consumers.
George and Tom’s goal, of course, is to drive Registered Caller to become the HTML of STIR/SHAKEN.
NOTE: To simplify our conversation, we use the term “telco” to refer to telecom service providers of all stripes: CSPs, carriers, VoIP providers, Over the Top (OTP) providers, mobile operators, wireline carriers and the rest. We will also use “enterprise” to refer to businesses, organizations, and companies making outbound calls.
| Dan Baker, Editor, Black Swan Telecom Journal: George, how do you assess the current progress of STIR/SHAKEN? |
George Cray, iconectiv: Dan, I agree with your thinking. We are only just beginning to realize its full potential. Yet STIR/SHAKEN has already enabled one huge change in U.S. regulatory policy that is not widely recognized:
Telcos now have greater control over which calls they block.
Before, they were strictly forbidden from blocking calls. A telco had to deliver every call that came across its network. The best they could do was alert the consumer — in some way — when they thought a call was spam.
But the regulatory environment has changed and broadened telco options. The new regulatory guidance says, “If you know it’s an illegitimate or spoofed call — and the caller ID fails authentication — you can go ahead and block that call.”
And while this is good news, it also raises a major challenge because the reality of STIR/SHAKEN today is that a lot of legitimate calls are hard to fully attest.
| Why is it so hard to attest or match up phone numbers with the enterprise who’s making calls? |
The simple answer is: managing enterprise phone numbers is far more complex than it used to be. Originating telcos must be able to determine who is making the call and that the calling party has the right to use that calling number before it can give full attestation to that call.
But with the advent of enterprises using VoIP, call centers, and having multiple telcos deliver their traffic, things are much more complex. For example:
- Many enterprises use multiple phone numbers for various outbound calling
purposes;
- External entities often manage those phone numbers for the enterprise
and;
- Call centers face greater complexity: they regularly place outbound calls
and manage the actual phone number assignment and the telcos who carry the calls
for their enterprise clients.
Usually, the originating telco isn’t the one who furnished the actual phone number itself. For example, many times an enterprise will alter the telco who delivers the outbound calling for a particular phone number.
So keeping track of the actual enterprise who is placing that call — and their right to use the number — is pretty hard to do. And that’s especially true in the VoIP world where many firms specialize in managing and assigning phone numbers to enterprises.
Given this complexity and the need for near real-time updating, very often a telco cannot attest a call accurately. And if you can’t attest — and the call doesn’t look like it’s from a legitimate caller — that’s when the called party may often let the call go to voice mail. But voice mail returns are unreliable today: some of us return our voice mails, but many others don’t.
This is where Registered Caller comes into play. When you have quality input from a trusted source that’s been vetted and verified, then both the originating and terminating provider can mark that as validated. So the consumer gains confidence that the caller is legitimate.
Registered Caller’s mission is to help establish the trust between legitimate enterprises and the consumers they are reaching out to by phone from all sources: wireline, wireless or toll-free numbers.
It’s about providing the full setup prior to the call — delivering all the verifying info on enterprise ownership of a phone number so it’s easy for the originating telco (through STIR/SHAKEN data exchange) to evaluate the call’s attestation level and better help the terminating telco determine whether to validate it, label it as spam, or block the call.
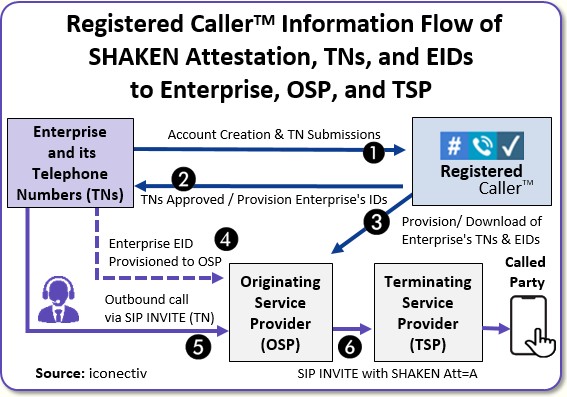
| So Registered Caller is a centralized system for collecting and managing info on enterprise ownership of phone numbers to help complement the utility of STIR/SHAKEN. But why is a centralized approach preferable? Can’t telcos and enterprises work out the necessary data exchanges on their own? |
Today, the ability for an originating telco to fully attest calls using STIR/SHAKEN is challenging because relying on the current system of scattered registries and analytic engines is not optimal. There are too many missing attestation gaps today, and that’s due to the complexities of phone number ownership we just discussed.
Having one common registry is ideal for getting consistent, vetted information to all participating telcos which will help call answering rates go up and make the whole experience better for consumers.
The way we built Registered Caller, enterprises themselves are the ones who register — or a call center on their behalf. And they pay a small fee which guarantees their information will eventually be available to all the telcos in the ecosystem that work with Registered Caller. So enterprises only need to enter their data in one place, not just the preferred analytic engine or partner a telco currently works with.
We don’t charge the telcos. We’re providing a common resource to the ecosystem so the telcos that work with Registered Caller will get all the information in a consistent fashion that benefits the enterprise. It will lower a telco’s overall costs as it improves their customers’ satisfaction. It helps telcos fill in the missing blanks for call authentication when they don’t know the enterprise making the call and/or its right to use the calling number being asserted.
Another great reason to centralize is to deliver the attestation data in a common format. For example, if you went to AT&T, they expected you to input the data in a certain way. The same goes for T-Mobile, Verizon, or other telcos, you had to deal with them all.
But as STIR/SHAKEN reaches wide adoption, the large mobile telcos are stepping back and said, “Listen, now that we’ve learned a bit about how this new tool works, there’s an opportunity to simplify.”
The telcos approached the idea and yes, the wireless telcos do indeed like the idea of a central registry.
And of course, in addition to being the administrator of LNP and policy administrator for STIR/SHAKEN, iconectiv has been working together and partnering with CTIA in the SMS Short Code Registry area, on behalf of those wireless telcos; so it was a good fit.
| Tom, what was the driving factor for CTIA supporting Registered Caller? |
Tom Sawanobori: Because it’s clear to us, Dan, that enterprises need a centralized place to do the things they want to do.
That’s the gap Registered Caller is addressing. Today, each of the telcos are doing it themselves by using third party tools which utilize solutions like scanning calling patterns and trying to figure out whether a call is legitimate, or should be marked spam or simply blocked.
Right now, calls may be marked as “unknown”. So the effect of that is I get multiple calls each day that are marked either “spam” or “potential spam”.
But that “spam” identified call could be from a doctor’s office, a school, or other firm that needs to get in touch with me. Yet in many cases, I don’t know who that is, because it’s not marked to identify who they are.

A recent study showed that 58% of consumers only answer calls from numbers or callers they recognize. But if your bank wants to notify you about credit card fraud, you need to know that number is trusted.
Same goes for a doctor’s office trying to explain some lab test results. Or it might be your child’s school calling saying kids need to be picked up early today — or whatever the urgent message is.
So this is where Registered Caller comes in and provides a centralized registry for the entire industry. They pay a small fee to have their numbers entered in the registry where they are vetted and validated to help ensure that when enterprises try to reach consumers, the call looks legitimate.
| Tom, your comment “enterprises need a centralized place to do the things they want to do” suggests enterprises are eagerly pushing the envelope on where STIR/SHAKEN goes in the future. |
Tom Sawanobori: They absolutely are, Dan. We are now engaging with the ecosystem to figure out the best ways to leverage STIR/SHAKEN. The enterprises are very excited about this and achieving certain goals:
- Improving accuracy is the first objective — Enterprises are eager
to have their calls both fully attested and legitimized in the eye of the consumer.
- Enterprises are looking at rich call data including enterprise name, logo,
and purpose of the call. This is especially key in urgent situations
such as a bank alerting you to fraudulent activity on your credit/debit card.
- Enterprises want consistency in the way their branding is presented to
the caller, i.e., name and abbreviations, logo and so forth. So
they are quite keen on making the information available to both originating
and terminating telcos.
George Cray: Tom, the availability of seeing rich call data during the call will also be a great help in public safety and first responder situations where they desperately need consumers to pick-up their calls.
In a CNN story I read last week: a hiker exploring the deep woods of Colorado didn’t check in by phone at the agreed upon time he was expected to be back at the camp.
So some concerned fellow-hikers called Search and Rescue Service (SARs) who tried to call him multiple times and he never answered his phone. When he eventually reappeared, he said he “never recognized the number.”
But in the meantime, Search and Rescue spent a lot of money and time looking for him. So as you can see, rich call data will help police, firefighters, emergency medical teams, and other first responders stay better informed and use their precious time more effectively.
| George and Tom, thanks for this fine briefing. Hearing about the enthusiasm enterprise and telcos have for leveraging STIR/SHAKEN further, I have high confidence in a few years we’ll see widespread adoption in advanced nations of the world. Good luck in your efforts. |
Editor's Note: Early on in this story we made an analogy between STIR/SHAKEN and the Internet. The table below is a quick event timeline in the development of the Internet. Notice that it took 15 years between the global internet's start (1983) and the arrival of the Google search engine (1998).
But while the Internet's adoption was relatively slow, once the right usability frameworks and common languages were set up (browsers, HTML, CSS, Javascript, and search engines), the Internet took off like a rocket:
Copyright 2023 Black Swan Telecom Journal
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


