| © 2022 Black Swan Telecom Journal | • | protecting and growing a robust communications business | • a service of | |
| Email a colleague |
April 2017
A Herculean Task: Battling Fraud in an Increasingly Complex Comms World

The myths of the ancient Greeks continue to teach us valuable lessons. Heroes such as Odysseus and Hercules were merely average men. They had every human weakness and made plenty of dumb mistakes, yet their smarts and adaptability allowed them to conquer even the toughest of opponents.
Take the case of Hercules. His mission was to kill Hydra, a multi-headed, serpent-like monster, but that wasn’t easy. For every time you succeeded in chopped off one serpent head, the Hydra would quickly grow back two heads to replace the one it lost!
And isn’t that a fitting metaphor for the fraudsters? As fraud control teams get better at cutting off one particular type of fraud, the fraudsters grow new fraud avenues and schemes to compensate for the loss.
Well, Michalis Mavis, consultant and former head of fraud control at OTE in Greece, is someone highly experienced at fighting fraud from multiple directions.
In my interview with Michalis, he walks us through some interesting cases, gives us his advice on FMS software, and offers four key lessons on the path to fraud management excellence.
| Dan Baker, Editor, Black Swan Journal: Michalis, it would be great to hear about your career in fraud control, and I understand the Olympics had something to do with it. |
Michalis Mavis: Yes, Dan, I got started in fraud management at OTE in the early 2000s. At the time, OTE was Greece’s government-owned operator: they have since gone private and are owned in part by Deutsche Telekom.
And the Olympics did play a key role! We launched our fraud management system just before the Olympic Games in 2004 which took place in Greece. Now, since I was president of the Hellenic Fraud Forum (HFF), I was privy to the fact that Greek operators experienced heavy losses at that time. In addition to OTE, we had Wind Greece, COSMOTE, Vodafone and other operators in the forum.
And since it was already reported in the newspapers, I can tell you that the fraud losses in Greece for that year were about 100 million Euros for all HFF member companies.
Fortunately I proposed to our CEO to start building a fraud control division and within a few months we bought the Hewlett-Packard FMS, a very good system. Soon thereafter, we cut our fraud losses at OTE by 50% and they were very significant savings.
| What kind of frauds did you experience there? |
Many different types, but the most significant at that time were PBX related. For example, Olympic Airways (previously owned by the well-known Greek millionaire Onassis) was hacked and the fraud cost them $5 million Euros in some weeks’ time. Then the National Nuclear Research Center Democritus, lost a half million Euros from frauds in only 3 weeks. The National Bank of Greece, the British Council in Athens, the ACS Courier and many other companies faced PBX fraud and were quite unaware of the fraud threat.
Now some say, “Why alert the big enterprises? When they get fraud, they have to pay the operator anyway.”
Well I think that strategy is bound to backfire. Even for a large enterprise, when the losses get heavy, the enterprise will often say, "Sorry we cannot pay you." So the telecom often ends up eating the cost.
It happens on the consumer side too. In one fraud case, young children at home were told to call a primary rate phone number advertised on television. And many times the father of the house couldn’t pay the bill because it was 20 or 30 times the normal amount.
The tricky part of that fraud was it appeared on the books as bad debt — not fraud — so it was important to communicate internally to close that gap and our FMS did a good job of resolving the issue.
| Criminal minds can be quite cunning. Is there a particular fraud case that stands out as highly usual? |
One of the more memorable fraud problems we saw was on the island of Crete, south of Greece. Crete is a big island and lots of tourists visit there each year. Crete was home to many immigrants from Syria, and the Syrian mafia eventually started operating there too.
So a company in Crete calls us and says they need 20 telephone lines. And as soon as they got those lines, they started making fraudulent international calls. We sent the first bill in some weeks time but it was never paid. Then they would close their shop, go to a new address, and start the same scheme again. Unfortunately no FMS was monitoring their accounts so we lost major revenue at first.
But once we did zero in on the case, we discovered them in two or three days time and we had the police arrest the leaders of the criminal ring, putting them in a Crete jail for six months.
Only a few months later another company calls us saying, “We are setting up an internet café business, we need 3 ISDN lines". Soon thereafter we noticed high rate IRSF calls were being made from those ISDN lines. And the calls were actually originating from the cardphone of the same jail in Crete where the criminal ring leaders were locked up.
The same guys were behind the fraud. They figured out how to connect special equipment to the ISDN lines and were making the international calls on one of the ISDN channels, by calling from inside the prison cardphones, selling international calls to other prisoners, and using fraudulent telecards.
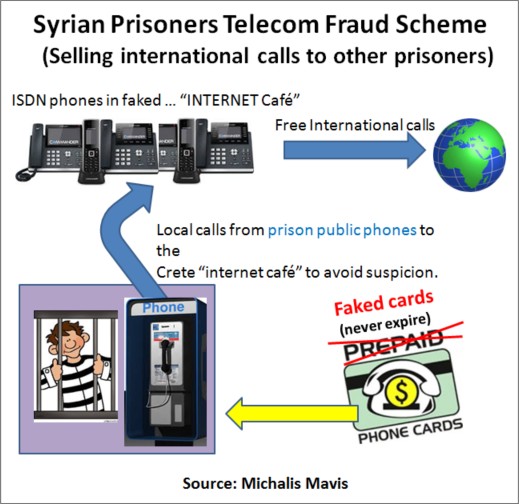
The trick the Syrian Mafia used in Greece was what the police called “playing the Joker” calling card. Those telecards were used in public phones that are found in the streets. The calling cards would decrement the charge for each call, but as soon as the card reached zero balance, it would be fraudulently reloaded with a new 30 Euro balance. So these cards would never expire.
| These were very interesting cases. What about the fraud of one operator against another? |
Well, the fraud done by criminal rings gets most of the attention, but quite a bit of fraud also occurs between telecom operators.
For example, mobile operators can manipulate the signaling information to avoid paying.
If I make a telephone call from Greece to United States and the call cost is 10 Euros; 5 Euros is taken by the Greek telecom and the rest goes to the US operator. But if an operator in the interconnect chain manipulates the SS7 information for an SMS, let’s say, then the originating point of that SMS is not known and there is no cost to be shared.
| FMS tools: what’s your experience with them? |
Actually, the FMS is an excellent tool, but it’s critical to program it properly. If the filters are good, then you can locate and target a wide variety of frauds.
Profiling and categorizing subscribers for their individual usage is very valuable. If you never speak no more than 30 minutes with someone or you don’t work on Christmas, Easter, or weekends, that’s valuable fraud prevention intelligence.
One of the first significant problems we found with our new FMS was not fraud at all, but revenue assurance problems with our digital exchanges. We found many mistakes in the CDR processing chain, CDRs lost, not correctly rated and many other issues there. So FMS can be a key tool for testing things, even though other systems exist today covering revenue assurance needs. Whenever a new version of the digital exchange is installed, new problems arise and the rating of calls has to be examined. The fraud management system is also of great assistance in solving these problems, especially in the first steps following the installation of the new system.
Networks these days are actually computers: the nodes of mobile networks, the home and visiting location register databases, the rater and the billing systems are all based on computer systems that can be manipulated and/or attacked. For this reason, security measures used in computer networks should be in place to guard against various threats.
Another important issue related to privacy is traffic analysis, which provides information on who is talking to whom and when. For example, if you know that I am talking to the US President, even though you don’t know what we are talking about, it is still significant intelligence. So it’s critical that CDRs be kept confidential and secured. That way, if someone hacks the mobile node, CDRs can be deleted, so traffic is not billed or stolen (allowing traffic analysis). In fact, a Denial of Service (DoS) attack can bring the whole mobile infrastructure down.
This is why the security of network equipment and hardware in the mobile system is very, very critical.
| What fraud control challenges do you see going forward? |
I think FMS systems need to step up and support both traditional circuit, VoIP services and new network platforms (IMS). There’s a need to combine CDRs with IP CDRs in one FMS. Modern systems are delivering many advances in this area.
We also need systems that take feeds from security modules: input from firewalls, IDS/IPS and security systems are most important now.
Television and video services from IP players like Netflix are expanding. And in those cases, people are paying for specific packages and there are intellectual property rights and QoS issues too.
So quality of service (QoS) issues have risen in importance. If I’m paying for a gold quality IP service, then I need to guarantee that traffic’s quality and ensure it’s being routed properly. And other big issue to monitor is Telco-OTT (Over-The-Top) fraud and the internet of things (IoT) and that will be everywhere, including your refrigerator and wearable gadgets.
Privacy violations are another big area where operators can run into trouble. We must build secure systems that protect CDRs and other sensitive data so it’s not disclosed to unauthorized people. And we also know that law enforcement needs access to certain information for lawful intercept reasons, such as identifying terrorist rings.
| When you consult with clients, what are the problems you see? |
Mainly I provide training courses in different countries, but as a follow-up to my training course, if they need some specific advice, I am happy to go in and fix them.
To generalize, I would say the problems are mixed. In some countries, you find people who have an inadequate fraud management system, built on very low value IT systems processing CDRs.
In other countries, the operator is equipped with an FMS, but those systems are not properly tuned. They are getting so many alarms that the really significant problems are not detected in time. This is a common problem where the fraud control division is under-staffed. If you have ten people looking at one thousand alerts per day, it’s hard to do keep track of that volume.
Dan, let me walk you through four key initiatives I’m passionate about. If you can do these four things right, I think you’re well on the road to fraud control excellence:
- Staff and Train your Company on Fraud
- Participate in International and National Forums.
- Conduct Technical and Procedure Audits.
- Be on the Lookout for Insider Fraud
Training the larger company is part of the mission of a well-organized anti-crime and fraud team. In particular, you need to give seminars to the senior executive team and CEO if possible. Otherwise, they will never know about the risks they face.
The training should also reach your internal teams, such as product management, technical folks and sales people.
Educate them on what happens globally, and emphasize proactive controls. For example, when launching a new product — a mobile service, a new bundle, whatever — examine the security and fraud issues in advance. If fraud issues are not baked into the design of a service, fraudsters may exploit those weaknesses — and you can lose a lot of money before you fully understand what’s happening.
There are several good international forums on fraud: the GSM fraud forum, FIINA (Forum for International Irregular Network Access), the CFCA, the Risk Assurance Group (RAG) and others. There’s even a European Union working group focused on fraud. And I always urge my colleagues to get involved in these groups.
Don’t think this is waste of time. As frauds jump from one operator to another, you are prepared because you’re sitting next to a person who will share threat information with you. Often these forums deliver cutting edge information you can take back to your team.
National fraud forums are also valuable. There’s one in Germany (DFF) and the UK (TUFF). In Greece I was the first chairman of the Hellenic Fraud Forum (HFF) formed back in 2000.
Auditing is another priority: you need to regularly assess your vulnerabilities. Also, your technical auditors should be audited for all the procedures of maintaining the mobile nodes.
The mobile infrastructure is nothing more than a mashup of computers. The HLR, VLR, mediation and billing systems, the rating engines — all of these blocks must be regularly audited.
Consider this: a mobile phone is either prepaid or post paid, and only one computer bit — a setting of 1 or 0 — determines how you treat a particular phone. And if that one bit is error, then a postpaid mobile phone will never issue a bill.
So this illustrates my point. Even if the bill is correct, there may still be problems with specific network equipment or devices.
Insider fraud is one of the biggest challenges today, yet people in many countries lack the knowledge to deal it.
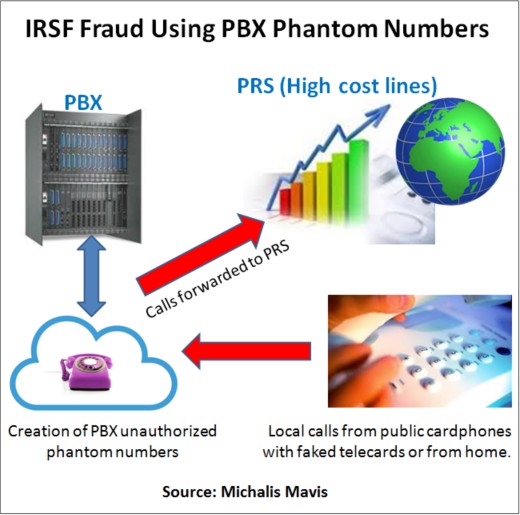
At an operator in Armenia, we were checking to see if the agreements with international carriers were being followed, or if people were bypassing traffic through other operators to get more money.
And at one point, we discovered an agreement from inside the company around the PBX service that made international and PRS (Premium Rate Service) expensive calls. They were making the calls by creating PBX phantom numbers. If a PBX has 500 extensions, it’s hard to figure out when new extensions are created without authorization. Then the new, unauthorized phantom numbers are used for IRSF fraud.
We were able to stop this big business of internal fraud. Inside fraud is very critical and it may represent very high losses.
And when you discover internal fraud, you should be very careful because the steps you should follow are different from what you follow whenever there is an outside fraud: it is very sensitive.
| Thanks for this great tactical advice, Michalis. I’m sure there are many operators out there who could use your help slaying the fraud monsters causing them pain. |
Copyright 2017 Black Swan Telecom Journal
Black Swan Solution Guides & Papers
- Expanding the Scope of Revenue Assurance Beyond Switch-to-Bill’s Vision — Araxxe — How Araxxe’s end-to-end revenue assurance complements switch-to-bill RA through telescope RA (external and partner data) and microscope RA (high-definition analysis of complex services like bundling and digital services).
- Lanck Telecom FMS: Voice Fraud Management as a Network Service on Demand — Lanck Telecom — A Guide to a new and unique on-demand network service enabling fraud-risky international voice traffic to be monitored (and either alerted or blocked) as that traffic is routed through a wholesaler on its way to its final destinations.
- SHAKEN / STIR Calling Number Verification & Fraud Alerting — iconectiv — SHAKEN/STIR is the telecom industry’s first step toward reviving trust in business telephony — and has recently launched in the U.S. market. This Solution Guide features commentary from technology leaders at iconetiv, a firm heavily involved in the development of SHAKEN.
- Getting Accurate, Up-to-the-Minute Phone Number Porting History & Carrier-of-Record Data to Verify Identity & Mitigate Account Takeovers — iconectiv — Learn about a recently approved risk intelligence service to receive authoritative and real-time notices of numbers being ported and changes to the carrier-of-record for specific telephone numbers.
- The Value of an Authoritative Database of Global Telephone Numbers — iconectiv — Learn about an authoritative database of allocated numbers and special number ranges in every country of the world. The expert explains how this database adds value to any FMS or fraud analyst team.
- The IPRN Database and its Use in IRSF & Wangiri Fraud Control — Yates Fraud Consulting — The IPRN Database is a powerful new tool for helping control IRSF and Wangiri frauds. The pioneer of the category explains the value and use of the IPRN Database in this 14-page Black Swan Solution Guide.
- A Real-Time Cloud Service to Protect the Enterprise PBX from IRSF Fraud — Oculeus — Learn how a new cloud-based solution developed by Oculeus, any enterprise can protect its PBX from IRSF fraud for as little as $5 a month.
- How Regulators can Lead the Fight Against International Bypass Fraud — LATRO Services — As a regulator in a country infected by SIM box fraud, what can you do to improve the situation? A white paper explains the steps you can and should you take — at the national government level — to better protect your country’s tax revenue, quality of communications, and national infrastructure.
- Telecom Identity Fraud 2020: A 36-Expert Analysis Report from TRI — TRI — TRI releases a new research report on telecom identity fraud and security. Black Swan readers can download a free Executive Summary of the Report.
- The 2021 State of Communications-Related Fraud, Identity Theft & Consumer Protection in the USA — iconectiv — This 49-page free Report on communications-related fraud analyzes the FTC’s annual Sentinel consumer fraud statistics and provides a sweeping view of trends and problem areas. It also gives a cross-industry view of the practices and systems that enable fraud control, identity verification, and security in our “zero trust” digital world.
Recent Stories
- Epsilon’s Infiny NaaS Platform Brings Global Connection, Agility & Fast Provision for IoT, Clouds & Enterprises in Southeast Asia, China & Beyond — interview with Warren Aw , Epsilon
- PCCW Global: On Leveraging Global IoT Connectivity to Create Mission Critical Use Cases for Enterprises — interview with Craig Price , PCCW Global
- Subex Explains its IoT Security Research Methods: From Malware & Coding Analysis to Distribution & Bad Actor Tracking — interview with Kiran Zachariah , Subex
- Mobile Security Leverage: MNOs to Tool up with Distributed Security Services for Globally-Connected, Mission Critical IoT — interview with Jimmy Jones , Positive Technologies
- TEOCO Brings Bottom Line Savings & Efficiency to Inter-Carrier Billing and Accounting with Machine Learning & Contract Scanning — interview with Jacob Howell , TEOCO
- PRISM Report on IPRN Trends 2020: An Analysis of the Destinations Fraudsters Use in IRSF & Wangiri Attacks — interview with Colin Yates , Yates Consulting
- Telecom Identity Fraud 2020: A 36-Expert Analyst Report on Subscription Fraud, Identity, KYC and Security — by Dan Baker , TRI
- Tackling Telecoms Subscription Fraud in a Digital World — interview with Mel Prescott & Andy Procter , FICO
- How an Energized Antifraud System with SLAs & Revenue Share is Powering Business Growth at Wholesaler iBASIS — interview with Malick Aissi , iBASIS
- Mobileum Tackles Subscription Fraud and ID Spoofing with Machine Learning that is Explainable — interview with Carlos Martins , Mobileum


